Managed Service Providers: Still Not Appreciating the Risk of Ransomware
Since June 2019, Managed Service Providers, IT service consultants and hosting providers have been increasingly targeted by ransomware actors. These attacks target the service provider’s remote management tools to increase the blast radius of the attack. When the attack is successful, every downstream endpoint at every client of the service provider is impacted.
In collaboration with NinjaRMM, Coveware surveyed a population of MSP organizations that had experienced a systemic ransomware event. These were events where the MSP’s own remote management tools were used by the attacker to encrypt the data of a large proportion of the MSPs clients.
This survey was done in conjunction with a survey by NinjaRMM of MSPs, most of which have likely never experienced a systemic ransomware attack. The intent was to better understand some key metrics associated with customer down time, cyber insurance coverage, customer attrition post-incident, and more. We found that there is a big disparity between expectations and reality. MSPs need to better prepare for potential attacks.
The total cost of a ransom attack: are MSPs estimating it accurately?
We asked MSPs that experienced a systemic ransomware incident:
What would you estimate the total cost of the incident to have been (inclusive of business interruption, IR vendors, any ransom payment, legal liability..etc)?
Over one third (35%) of respondents who had experienced a ransomware event cited financial damages in excess of $1,000,000. This is in contrast to the 40% of respondents in NinjaRMM’s data that indicated they could not endure more than $500,000 in damages and the 23% who could not withstand even $50,000.
This disparity highlights a persistent and troubling disconnect between the realistic financial setbacks of an extortion event, and what organizations perceive the costs to be.
Cost Business Could Sustain vs. Actual Cost
Source: NinjaRMM
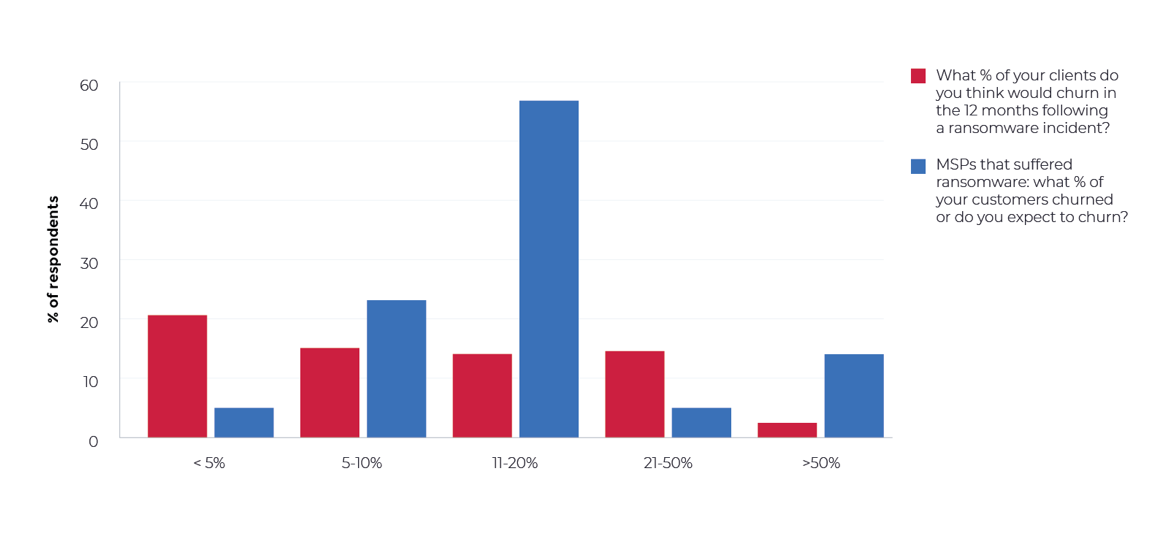
Are MSPs aware of how many customers they may lose following a Ransomware Attack?
We asked our prior MSP clients:
Following the incident, what % of your customers churned, or do you expect to churn?
When asked to estimate with percent of their customer base churned following a ransomware event, the majority (57%) of respondents reported a percentage in the 11-20% range. Very few estimated that they avoided attrition altogether, and 13% reported aggressive churning rates of 50% or higher.
Overall, the rates of actual customer loss exceeded the expected rate of loss estimated by most MSPs surveyed by NinjaRMM who had yet to experience an incident. This disconnect suggests MSPs are still experiencing a learning curve when it comes to projecting the fallout of a ransomware attack that extends to their end customers.
Client Loss Following Ransomware: Expectations vs Reality
Source: NinjaRMM
Downtime after ransomware attacks: What is the reality?
End client downtime and customer churn are closely correlated. We asked MSPs that have been through a ransomware incident:
How much downtime did your most impacted clients experience as a result of the incident?
Downtime following a cyber incident is one of the most complex and ever-evolving metrics. It has steadily increased over the past several years due to a handful of critical variables, including but not limited to:
The nature of the victim’s business;
The number of systems and locations impacted;
The availability of technical resources;
The presence or absence of secondary threats within the network; and
The status of the victim’s backups for mission-critical data.
Over half (52%) of respondents reported that their highly-impacted customers experienced 3-6 days of business interruption as a result of the ransomware attack. About a third (30%) cited longer interruptions lasting 7-14 days; notably, zero respondents indicated they were able to limit downtime to 48 hours or less.
In the current threat climate, containment is more necessary than it has ever been - not only to combat the threat actors that deployed the ransomware (who may be hanging around post-attack), but also to eradicate the secondary and tertiary threats that were deployed days or weeks in advance of the attack itself. Even in the absence of these side effects, recovery can be a sluggish endeavor, whether it’s a result of expected lag time in backup restoration or a byproduct of a poorly-configured decryption tool.
Ransomware & Downtime: Expectations vs. Reality
Source: NinjaRMM
Do MSPs have the staffing resources to recover their end clients?
Labor tends to be a common choke point in the recovery process for any ransomware attack. We asked MSPs that have had to recovery their clients from ransomware:
Did you have sufficient staffing to handle recovering from the incident?
It came as little surprise to learn that the majority of respondents (65.2%) advised they had insufficient personnel resources to respond to the event, and were forced to allocate resources to some affected clients before others. This can be especially complex for providers who must explore the decryption option, as some ransomware variants generate unique decryptors for every machine in lieu of a one-size-fits-all master decryption solution.
Coordinating the decryption effort across dozens of machines is cumbersome enough for a single organization; multiply that by an entire customer base, and you are in for a long, fraught road to recovery.
Ransomware insurance: Are MSPs covered against attacks?
Given the financial damage that a ransomware attack can cause, mitigating the risk would seem to be prudent. We asked MSPs:
Did you have a cyber policy, and if so how much coverage did you have?
On the subject of cyber insurance, Coveware’s data revealed a range of responses. On one end, 35% of participants reported that they had no coverage at the time of their incident. At the other side of the spectrum, another 35% reported having a policy of $2,000,000 or more in coverage. When we consider that the risk profile for an MSP is exponentially higher than that of most single entities, the hope is that the overwhelming majority of these providers will engage suitable levels of coverage before they or their customers experience an incident.
Most MSPs are not ready for a systemic ransomware attack
The data points from MSPs who have felt the impact of a ransomware event and its associated outcomes, compared to MSPs who had never encountered a ransomware event are striking. The datasets showed a marked divide between what organizations expect and what actually occurs, particularly in respect to customer attrition and downtime immediately post-incident.
MSP based attacks have been occurring now for over a year and a half, and unfortunately will likely continue. We encourage all MSPs to recognize the risk of these events. Talk to your peers that have been through the experience to understand the risks. And please...pretty please, use Multi-Factor Authentication on all your important tools and keep your patches up to date!