Decrypting Gandcrab Ransomware: Payment and Recovery Guide
UPDATE: Most versions of GandCrab Ransomware can be decrypted with free tools. Please click the below button to visit our partners at No More Ransom to download the version you need!
GandCrab has been circulating in many different forms after the past 2 years. This type of ransomware made headlines for the creators' very public feud with Bitdefender, and for the investment in distribution and payment technology that the owners have made. Currently, v5 uses an intuitive payment portal via unique TOR sites for each attack. The sites offer several features that demonstrate the group's focus on profitable conversion of their attacks. We will go through those features below (also see our dedicated GandCrab page for pricing, decryption and data recovery trends).
Like most types of ransomware currently circulating, GandCrab typically leverages hacked Remote Desktop Protocol (RDP) access as the means for ingress. The hacker first gains access by:
Purchasing previously brute-forced credentials from sites like XDedic.
Phishing an employee of the company to gain control of their machine, then using access to brute force from inside the network.
Brute forcing RDP ports found on search sites like Shodan.
The public and lateral access conveyed by RDP enables the hacker to comprehensively spread the ransomware across a multitude of devices like individual machines, servers, and backup systems. Additionally, recent variants like .combo are using a complicated two-step decryptor tool.
A step-by-step Rundown of a GandCrab Ransomware Attack
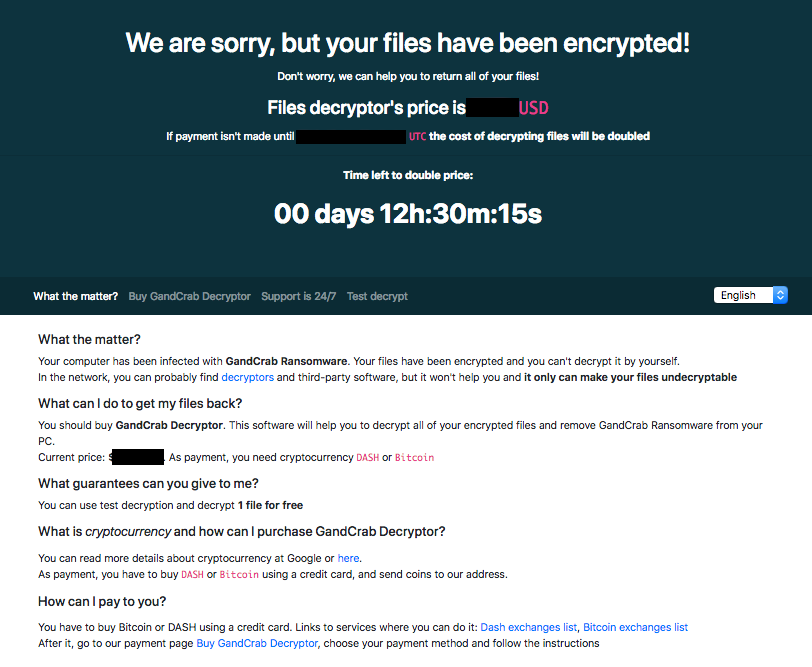
The Tor Site
An infected machine or group of machines will display a randomized set of file extensions on encrypted data. Unlike prior versions which utilized the .crab brand, this version better evades some AV tools by creating unique randomized file extensions for each attack. A {}.decrypt.txt file is dropped on the encrypted machine with the unique randomized digits at the start. The file provides instructions on how to visit the tor site. The site itself has four tabs under its navigation.
Tab 1: Ransomware Message with Relevant Links
This page can be toggled into 8 different languages, provides the ransom amount and a live counter with notes on the price escalation terms. As usual with ransomware notes they try to provide some useful links on how to quickly acquire cryptocurrency for payment.
Tab 2: Ransomware Payment and Decryption Instructions
The site allows payment in either Bitcoin or Dash, and a user can toggle between either currency, which updates FX rates and wallet addresses. This current version charges a 10% premium for payments made in Bitcoin vs Dash due to costs the hackers incur mixing bitcoin after collection. When a payment is made correctly, the site detects the wallet that matches the payment terms, and the payment shows up at the base of this tab. After 3 confirmations (20-30 minutes after payment), an interstitial pops up on this page upon refresh with a link to download the decryptor and instructions on how to use it. For clients that we have assisted, the data recovery rate is 100%, though the decryptor runs slower than others we have worked with and is prone to crashing. We also note that incident response firms that frequent these pages are offered a discount code that can be applied to the checkout page (we pass this discount on to our clients with 100% transparency).
Tab 3: 24/7 Chat Support For Communicating With Hackers
There is also a call to action for data recovery firms to receive a discount code (mentioned above) which can be used on future settlements. They do provide a stern warning that if they see the code on any public forums, it will be blocked. In our recovery work, we have used this chat box at all hours of the day and week, and have experienced almost no latency in responsiveness. We have even been transferred to a new support person between their shifts with no loss of support. Frankly, it is a bit scary how good they are at support - but for good reason: they recognize that good support equals payment conversion. This is simply a sales funnel and the faster the conversion cycle the better for them.
Tab 4: Testing Tool For The Decryptor
On the ‘Test decrypt’ tab, a user can upload an encrypted file and receive the decrypted result with almost no latency.
Coveware’s Closing Thoughts on GandCrab:
This payment front end is a scary vision of deep technical and organization design work - a major investment of human and financial capital by the hacker groups to scale collection of ransomware payments. The pace of iteration we have observed is also measured in weeks, as new variants of the malware are released and improvements to the front end make attacks cheaper to stage and more profitable to collect on. As we assist more and more clients with ransomware recoveries, one thing is clear. The gap between who is winning and losing this battle is rapidly expanding.
If you need help decrypting GandCrab ransomware or any other variant please don’t hesitate to reach out for help.