Decrypting Dharma Ransomware: Quick Recovery Guide
Dharma ransomware has been around for a few years with lots of files. Over the past three months, hackers using the .BMP, .BIP, and .COMBO variants have been very prevalent. Like several other types of ransomware, Dharma leverages open or weakly-secured RDP ports to gain network access. Access through RDP is usually achieved by:
Purchasing previously brute-forced credentials from sites like XDedic.
Phishing an employee of the company to gain control of their machine, then using access to brute force from inside the network.
Brute forcing RDP ports the are found on search sites like Shodan.
The public and lateral access that RDP conveys, enables the hacker to comprehensively spread the ransomware across a multitude of devices like individual machines, servers, and backup systems. Additionally, recent variants like .combo are using a complicated two-step decryptor tool.
Data Recovery Complications. Does Dharma Ransomware Decrypt Easily?
When recent Dharma ransomware variants are paid, and the decryptor tool provided by the hacker does not decrypt files immediately. The victim must first run the tool to produce a scan key. The Scan key is then sent back to the hacker. The hacker uses this unique scan key to generate a unique decryption key. This extra step can materially complicate recovery of large, partitioned networks of servers, backups, and individual machines. Communication language barriers, differing time zones, and unclear demands and instructions can also exacerbate the severity of an attack and compromise data recovery efforts.
If a single encrypted machine is scanned, and then decrypted by the tool, the recovery can be relatively straight forward. Complications can arises though if the malware is not properly removed prior to running the tool, or if anti-virus programs are not properly disabled, or removed prior to running decryption. If the decryption is only partially successful, or if the malware is not properly removed causing the files to become re-encrypted. The original decryption key will no longer work. This is because the modification to the files, however minor would produce a different different scan key and then require a correspondingly new unique decryption key from the hacker.
To the hacker, this new scan key seems like a new machine that the company is requesting to be decrypted, as Dharma has not historically involved communication with a C2 server, and recent cases have not reported outbound network traffic that would insinuate otherwise. Since a the hacker controls access to new decryption keys for each scan, it can allow the hacker to attempt to extract multiple payments for each key needed.
This logistical twist can create material permutations in the outcome if the hacker requires a new payment for each scan key. This is especially acute if the victim is not aware of the consequences of requesting multiple keys ahead of time.
The Two-Step .Combo Dharma Decryptor Tool:
(Please note that the below is just an example and not a guide or guarantee that should be relied on in any way. Ransomware variants and their decryptors evolve weekly and this example may be obsolete or conflict with instructions a hacker provides. Please see our Terms of Service for further disclaimer)
After paying a hacker and receiving the decryptor tool from the hackers, the victim is instructed to ensure that the virus executable is turned off or removed, otherwise the files will just get re-encrypted. AV must also be disabled or completely removed. The tool must be run as an administrator.
The first step after downloading and opening the tool is to run a scan. The below image is where a user would start by pressing ‘Scan PC’
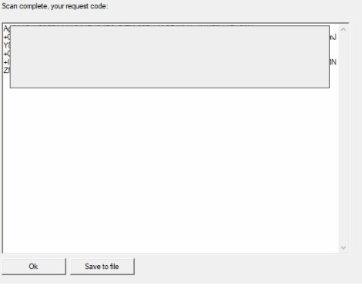
The user can map to a specific drive or scan the entire machine if left blank. After the machine is scanned, a scan key is displayed in a text box of the tool, similar to below.
The scan key can either be copied or downloaded as a .txt file. The hacker instructs the victim company to send each unique scan key to them, and for each scan key, replies with a unique decryption key. The decryption key provided will only work on the machine that created the corresponding scan key.
When the decryption sent back, the user clicks the ‘Decrypt’ button, and the decryption key is pasted into the open text box of the tool.
The user is given the option to delete and overwrite the encrypted files in the checkboxes. In our experiences, these boxes need to be checked, otherwise the tool fails to decrypt files. Depending on the size of the machine, this can take minutes or hours for the decryption to complete.
If you are experiencing a ransomware incident involving Dharma or any other variant please don’t hesitate to reach out for help.