Ransomware Costs Double in Q4 as Ryuk, Sodinokibi Proliferate
Coveware’s Q4 Ransomware Marketplace report aggregates anonymized ransomware data from cases handled and resolved by Coveware’s Incident Response Team, and other Incident Response firms that utilize the Coveware Incident Response Platform to manage their own cases. This report discusses data points like the average ransom amounts, data recovery rates, and ransomware attack vectors. Unlike surveys, which rely on sentiment, this report is created solely from a standardized set of data collected from every case. By aggregating and sharing this data we believe large and small enterprises can better protect themselves from the persistent and ever-evolving ransomware threat. Please don’t hesitate to reach out to us with any questions or comments. Thank you for reading!
How Much Does a Ransomware Attack Cost?
The total cost of a ransomware attack is a function of the severity and duration of the attack. Financial costs include the the ransom payment if one is made, and the costs to remediation of a network and its hardware. Costs also include lost revenue and potential brand damage if business interruption is severe enough. In Q4, ransomware actors also began exfiltrating data from victims and threatening its release if the ransom was not paid. In addition to remediation and containment costs, this new complication brings forth the potential costs of 3rd party claims as a result of the data breach.
What Is the Average Ransom Payment?
In Q4 of 2019, the average ransom payment increased by 104% to $84,116, up from $41,198 in Q3 of 2019. While the median ransomware payment in Q4 was $41,179, the doubling of the average reflects diversity of the threat actors that are actively attacking companies. Some variants such as Ryuk and Sodinokibi have moved into the large enterprise space and are focusing their attacks on large companies where they can attempt to extort the organization for a seven-figure payout. For instance, Ryuk ransom payments reached a new high of $780,000 for impacted enterprises. On the other end of the spectrum, smaller ransomware-as-a-service variants such as Dharma, Snatch, and Netwalker continue to blanket the small business space with a high number of attacks, but with demands as low as $1,500.
How Much Data Is Recovered After Paying a Ransom?
When a ransomware victim is forced to pay a ransom, there are two success metrics that determine the outcome. First, does the payment result in a working decryption tool being delivered? If the threat actor did not deliver the tool, then it is considered a default and will likely lead to a 0% data recovery rate. Second, if a working decryption tool is delivered then how effective is it in decrypting the data? Files and servers can be damaged during or after the encryption process and this can affect data recovery rates even when a decryptor tool is delivered.
How Often Is a Decryption Tool Delivered After Paying a Ransom?
In Q4 of 2019, 98% of companies that paid the ransom received a working decryption tool. This is flat with Q3 of 2019. Payment success rates do vary across different types of ransomware and different threat actor groups. For instance, certain threat actor groups associated with Phobos, Rapid and Mr. Dec ransomware that are known to consistently default after being paid. Any victim of ransomware should seek out information about the variant and threat actor before ever contemplating a payment.
Do Ransomware Decryptor’s Work?
In Q4 2019, victims who paid for a decryptor successfully decrypted 97% of their encrypted data, a slight increase from Q3. The most prevalent types of ransomware such as Sodinokibi and Ryuk are being distributed by more sophisticated actors, who tend to be more careful in how they handle the encryption process. While that may seem contrary, we tend to see better outcomes with more sophisticated attackers. Less sophisticated attackers have a higher likelihood of deploying payloads in an irresponsible manner that corrupts data beyond recovery. We have seen certain Ransomware-as-a-Service groups actually become very selective about who they allow becoming a distribution affiliate. This can limit the scope of their earnings but allows them to control the reputation of their ransomware, which in the long run may result in higher profits from their criminal efforts.
How Much Downtime Does a Ransomware Attack Cause?
In Q4 of 2019, average downtime increased to 16.2 days, from 12.1 days in Q3 of 2019. The increase in downtime was driven by a higher prevalence of attacks against larger enterprises, who often spend weeks fully remediating and restoring their systems. Established enterprises have more complex networks, and restoring data via backups or decryption takes longer than restoring the network of a small business. Additionally, certain actors such as Ryuk have evolved their attacks to make them even more pervasive. In Q4 Ryuk actors began using a “Wake-on-Lan” feature to turn on devices within a compromised network that were initially powered off. This greatly magnifies the impact of the attack. Ransomware is typically detonated during the night or early morning hours when oversight from security admins is limited. Infiltration during off-peak hours means that most machines are not running as the workday is over and most employees are gone. This feature turns their machines back on so that the number of encrypted endpoints is maximized.
What Cryptocurrencies Are Used to Pay for Ransomware?
Bitcoin is used almost exclusively now in all forms of cyber extortion. Cyber criminals have realized that it is easier to swap extortion proceeds into a privacy coin after they collect, then to require a victim to purchase a less liquid type of digital currency. Inside an extortion incident, the victims' problems are the extortionists’ problems. Procuring cryptocurrency quickly remains a challenge for victims in need, which means it is a barrier to success for the cyber criminals as well. Accordingly, the criminals try to lower as many barriers as they can. Denominating in bitcoin vs. Monero or Dash is the path of least resistance.
What Are the Most Common Types of Ransomware?
In Q4 2019, Sodinokibi was the most prevalent type of ransomware by incident count. Sodinokibi is Ransomware-as-a-Service, but only allows a select number of affiliates to distribute the ransomware. There is at least one Sodinokibi affiliate in particular with a deep specialization in compromising and exploiting the remote monitoring and management (RMM) tools used by IT managed service providers (MSPs). Once compromised, an MSPs RMM tool is used to push the ransomware executable to every endpoint managed by the MSP, greatly magnifying the impact of the attack. It is not uncommon for an MSP to have hundreds of individually impacted end clients if Sodinokibi is successful in gaining persistence within the MSPs network. During the quarter, Sodinokibi also changed their extortion tactics to include threatening the release of exfiltrated victim data.
Ryuk Ransomware continued to plague large enterprises during Q4, and was again the second most common type of ransomware. The average Ryuk ransom amount rose dramatically though, and accounted for the majority of the change in the average ransom payment doubling during the quarter. The group also changed their post breach lateral proliferation tactics slightly, as detailed below.
Phobos and Dharma also continue to be a steady portion of small enterprise ransomware attacks. These ransomware-as-a-service operations are available to any cyber criminal at no cost. The free access combined with cheap RDP credentials has dramatically lowered the bar for entering the cyber crime industry.
What are the Most Common Ransomware Attack Vectors?
In Q4 2019, ransomware distributors continued to prove that they are economically rational. The mass availability of Remote Desktop Protocol (RDP) credentials to corporate networks for as little as $30 per IP address has made carrying out a targeted attack extremely cost-effective for the attackers. Until the economics of these attack vectors change, ransomware will continue to proliferate and grow in popularity as a form of cyber crime. We also saw several high profile software vulnerabilities being exploited by the Sodinokibi affiliates. Most notable, an unpatched vulnerability in the Pulse Secure VPN was exploited allowing remote attackers, without valid credentials, to remotely connect to the corporate network. After infiltrating the network, attackers disabled multi-factor authentication, and remotely viewed logs and cached passwords in plain text, including Microsoft Active Directory account passwords. To a ransomware actor, this vulnerability was the equivalent to a golden ticket. For larger enterprises, email phishing continues to be the preferred method of initial compromise. A phished employee can easily serve as the initial staging point for malware deployment, privilege escalation, lateral surveillance, and finally domain admin compromise.
Comparing the Top Three Types of Ransomware by Attack Vector
Ransomware attack patterns change year over year, but month to month they vary only slightly. When attackers find cost efficient methods to penetrate large populations of companies, they repeatedly exploit these avenues until they dry up. During Q4, the lower end ransomware-as-a-service variants such as Dharma and Phobos continued to exploit cheap and easy attack vectors like RDP. The more sophisticated groups like Sodinokibi also use RDP when available, but have also been observed exploiting more technically complex CVE’s, and using email phishing.
Comparing the Top Three Types of Ransomware by the Size of the Victim Company
In Q4, there were only mild shifts in attack patterns among the top three types of ransomware, but some large shifts in TTPs within the subcategories of the attack. Ryuk attackers continue to leverage email phishing to gain an initial toe hold inside a network before escalating their privileges. In Q4, the group was seen using PSexec to push the ransomware payload out to endpoints, but also shifted to using changes in Group Policy Objects (GPO) to both relaunch encryption, and tried to maintain persistence by previously scheduled tasks. Ryuk was also observed using a feature called ‘Wake-on-Lan’ to turn on computers that were initially powered off to ensure widespread encryption.
The size of victim companies correlates to the sophistication and attack budget of the cybercriminals. Less sophisticated and less well-financed attackers will target the lowest hanging fruit of companies below the cybersecurity poverty line. These companies are relatively easy to encrypt, but rarely offer the size of the payout that larger organizations (that are harder to attack) may pay. At the lower end of the market, widely available ransomware-as-a-service variants like Dharma/Phobos exemplify this. On the other end of the market, Ryuk attacks continue to target large enterprises that don’t have cheap attack vectors available. In tangent, Sodinokibi’s focus on MSPs results in large payouts, but relatively small victims sizes, as most companies that utilize MSPs are small enterprises with less than 200 employees.
Comparing the Top Three Types of Ransomware by Ransom Amount
Ryuk continued to push the limits during Q4 in a reversal of the trend from Q3. In Q3, we saw Ryuk groups take their attacks further downmarket. In Q4, they seemed to focus again on only the largest enterprises, and the scale of their demands reflected that. The average Sodinokibi ransom decreased dramatically as the affiliates failed to coerce large single payments from MSPs, and rather had to settle for small individual payments from the end clients of the MSPs.
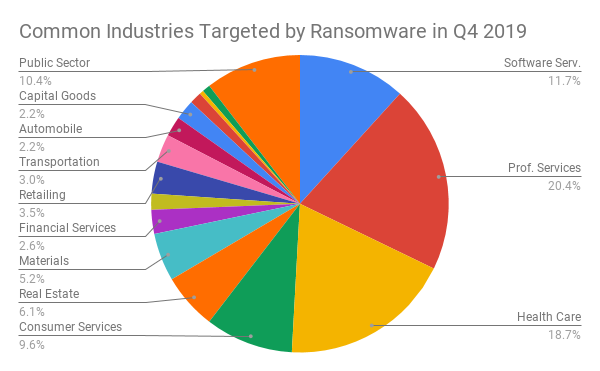
What Industries Are Commonly Targeted by Ransomware?
In Q4, public sector organizations continued to account for an elevated portion of ransomware attacks, albeit down slightly from Q3. Until these organizations are able to rightsize their IT security budgets and IT headcount, these attacks will continue. Healthcare organizations came back into focus in Q4 for both Sodinokibi targeting specialized service providers within healthcare, and variants like Defray 777 focusing all their attacks on the industry. Interestingly, some ransomware variants, such as Maze have publicly announced that they will not attack organizations where a disruption to patient care may cause the loss of life. Professional services firms such as regional law firms, consulting firms and IT service providers continue to make up the largest segment as an industry.
What Was the Average Size of Companies Targeted by Ransomware?
In Q4 of 2019, the average company size decreased to 610 employees, down from 645 in Q3. This decrease reflects the higher preponderance of individual victims of Sodinokibi MSP based attacks. It is not uncommon for a single Sodinokibi attack to create hundreds of individual small business victims.
Disclaimer:
Coveware is not responsible for any actions taken, errors or omissions (negligent or otherwise), regardless of the cause, or for the results obtained from the use of this content, or for the performance of any computer, hardware or software used or modified in conjunction with this content. The content is provided on an "as is" basis.
VIEWERS OF THIS REPORT AND ITS CONTENT DISCLAIM ANY AND ALL EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, ANY WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE OR USE, FREEDOM FROM BUGS, SOFTWARE ERRORS OR DEFECTS, THAT THE CONTENT'S FUNCTIONING WILL BE UNINTERRUPTED OR THAT THE CONTENT WILL OPERATE WITH ANY SOFTWARE OR HARDWARE CONFIGURATION.
In no event shall Coveware be liable to any party for any direct, indirect, incidental, exemplary, compensatory, punitive, special or consequential damages, costs, expenses, legal fees, or losses (including, without limitation, lost income or lost profits and opportunity costs or losses caused by negligence) in connection with any use of the content even if advised of the possibility of such damages.
Some images designed by ITIM2010 from Flaticon.