Uber Verdict Raises New Risks for Ransom Payments
Unpacking the Uber Verdict
Shortly after the end of Q3, Joe Sullivan, the former Uber CSO, was convicted of two felonies associated with the handling of a security incident that occurred in 2016. An aspect of the case against Sullivan was how extortion payments to the threat actors responsible for the 2016 hack were handled. While many of the critical facts and circumstances are unique to Uber and well beyond the average ransomware attack, there are some elements of the case that are worth unpacking. We want to emphasize that our analysis has the obvious advantage of hindsight. We look backwards not to judge, but to understand past and present events so that we may better navigate the future.
*Please note that this was not written by lawyers, reviewed by lawyers, and should not be construed as legal advice!
As a thought experiment, let’s imagine we were to plot cyber security incidents on a spectrum that gauges impact vs. legality of the attack. On the green end of the spectrum we could envision a company receiving a responsible disclosure of vulnerability via an established bug bounty program; there is no measurable impact from this event. Another example, in lieu of a company having an organized bounty program, would be a responsible disclosure program where security researchers have an observable vulnerability disclosure process. In both of these examples the security researchers are not breaking any laws. They are not exfiltrating data from private machines, and they are not manipulating or disturbing private company assets in a manner that violates laws.
On the other end of the spectrum, we can envision a full blown encryption and data exfiltration ransomware attack; these events are red, have major impact and clear cut violations of the law. In the picture below, the gauge is pointing to somewhere in the middle; around the line where the CFAA or other laws are crossed and the motives of the threat actor crosses from legal/responsible to illegal/extortionist.
The ‘orange’ section is where things get foggy and where there is risk of misclassifying a bonafide security incident and not responding appropriately. Situations in this middle ground may in fact be responsible disclosure events, but are construed as attacks. For example, consider a public facing site that has inadvertently stored private information without a user needing to break the CFAA to view it. Alternatively, consider a database of customer information that is open to the internet. Just because the database is wide open and easily accessed, does not mean that crossing the threshold, and exfiltrating a copy is legal.
We can easily imagine how these ‘orange’ incidents could be handled inappropriately without the right people doing the right legal analysis. So what should companies do when confronted with ‘orange’ incidents? Well, every incident is unique, but there are some general rules to follow that can keep companies out of trouble:
If the actor that performs the disclosure violated the law, you should treat them as a criminal. Legitimate functions like a bug bounty program, or non-disclosure agreements are not viable options for criminals (if they were, those channels could have been used to begin with).
If the incident in question creates notification obligation, regardless of the legitimacy of the actor, then you need to consult with competent privacy counsel in order to ensure you meet your notification requirements. The actor’s methods don’t have to be criminal to create notification obligations.
Transparency and communication of incidents to the (pick your corporate acronym) executive / cyber response team need to be reflexive, not discretionary. Don’t have a defined emergency response team? See bullet #4
If you are not clear on the answer to bullet #1, #2 or #3, you absolutely, unequivocally need to consult with outside counsel.
It is normal and reasonable for companies to face an ‘orange’ incident and not know what to do. Every incident has unique facets and may not fit neatly in a given security policy. This is where unwritten company culture fills the gap. A company’s culture is one of the most predictive indicators of both incident frequency and severity. Unfortunately, Uber’s cultural shortcomings were well documented at the time of the 2016 incident in question. Tom Uren provided a handy summary of other Uber initiatives in play during this period that are indicative of Uber’s culture:
“Uber allegedly used a "kill switch", for example, to prevent police and regulators from accessing Uber's corporate data in several countries when its offices were raided. And it is also accused of creating a tool known as "Greyball" that was used to identify and shadowban officials that were trying to regulate Uber. Australian officials say that because of Greyball they had to negotiate with banks and phone companies to obtain new bank accounts and SIM cards to investigate Uber's activities.”
There are lots of ways to make matters worse when triaging a security incident. Misclassifying an incident by accident is problematic, but misclassifying an incident on purpose is much worse. If company culture fluidly enables purposeful misclassification of security incidents then the legal risk of these incidents compounds.
Rarely does a single aspect of any incident cause the sum total of the measurable impact. Deeply impactful incidents are almost ALWAYS the result of compounding failures (i.e one mistake does not cause the resulting impact….several mistakes blended together do). When a company has a weak culture of security, compounding happens with very little friction, and impact can mushroom quickly.
Similarly, paying a ransom exponentially increases the compounding effect of impact. Victims of data exfiltration almost always underestimate the negative compounding effects of paying a ransom. While the damage that a data breach can cause a company is generally quantifiable, the impact caused by the compounding effect of a data breach + a ransom payment to suppress visibility and data breach notification is much more volatile. What we can infer from experience is that the best case scenario envisioned by a victim paying a ransom that aims to suppress a leak is often substantially the same as if they were NOT to pay. However, the worst case scenario of paying to suppress a leak is orders of magnitude worse than if the company had not paid.
If the downside risk is wildly asymmetric, but the upside is negligible, why do companies continue to pay threat actors to suppress data breaches? To put it simply, shame is a powerful emotion, and threat actors know how to use it to their advantage. If a company's culture enables shame and deceit to drive security incident handling, then they should not be surprised when compounding effects of these incidents culminate into situations similar to Uber’s.
Average and Median Ransom Payment in Q3 2022
Average Ransom Payment
+13.2% from Q2 2022
Median Ransom Payment
+15.5% from Q2 2022
The average ransom payment increased +13.2% from Q2 2022 to $258,143. While the average was pulled up by several outliers, the median ransom payment actually increased to $41,987, a 15.5% increase from Q2 2022. This trend reflects a consolidation of ransomware as a service (RaaS) groups impacting the middle market.
Most Commonly Observed Ransomware Variants in Q3 2022
| Rank | Ransomware Type | Market Share % | Change in Ranking from Q2 2022 |
|---|---|---|---|
| 1 | BlackCat | 15% | - |
| 2 | Hive | 13.5% | +1 |
| 3 | Black Basta | 6% | +2 |
| 4 | Dark Angels | 3.8% | New in Top Variants |
| 4 | Phobos | 3.8% | +1 |
| 5 | Vice Society | 3% | New in Top Variants |
| 5 | AvosLocker | 3% | - |
Market Share of the Ransomware attacks
The prevalence of Hive ransomware during the quarter increased materially, rising from ~6% of attacks in Q2 2022. As threat actors have become more fluid, we are consistently seeing overlap between RaaS affiliates and the RaaS brand they choose to use for a specific attack. In some cases, we even see affiliates attempting to double extort a victim by pretending to be two different groups that impacted the company (2 sets of encryption). In reality, the attack was handled by a single affiliate that carried a payload from two different RaaS brands into the network and used both.
Ransomware Attack Vectors and MITRE ATT&CK TTPs Observed in Q3 2022
Initial Access: [TA0001]
Initial access vectors began to blend in Q3 of 2022 as threat actors have further embraced a ‘live off the land’ philosophy of monetizing access types as they become opportunistically available versus committing to a certain vector. The ‘unknown’ vector increased in Q3 as conclusive evidence confirming the initial vector becomes hard to pin down with a greater prevalence of malware-less email phishing campaigns and hardware CVE’s that have broad coverage. The ‘internal’ category also made an appearance on the radar for the first time as a measurable subset of attacks observed insider or insider aided initial access.
TTPs
Impact: [TA0040] Impact consists of techniques used by adversaries to disrupt availability or compromise integrity of business and operational processes. Techniques used for impact can include destroying or tampering with data. In some cases, business processes can look fine, but may have been altered to benefit the adversaries’ goals. These techniques might be used by adversaries to follow through on their end goal or to provide cover for a confidentiality breach.
Data Encrypted for Impact [T1486] Encryption of files is the most common form of impact observed. This may include forensics logs and artifacts as well that may inhibit an investigation.
Data Destruction [T1485] Most of the time, data destruction is aimed at the destruction of forensic artifacts via the use of SDelete or CCleaner. Unfortunately, sometimes ransomware actors destroy production data stores (sometimes malicious, sometimes by accident).
Lateral Movement [TA0008]: Lateral Movement by threat actors consists of techniques used to enter and control remote systems on a network. Successful ransomware attacks require exploring the network to find key assets such as domain controllers, file share servers, databases, and continuity assets that are not properly segmented. Reaching these assets often involves pivoting through multiple systems and accounts to gain access. Adversaries might install their own remote access tools to accomplish Lateral Movement or use legitimate credentials with native network and operating system tools, which may be stealthier and harder to track. The 3 most observed forms of lateral movement are:
Remote Services [T1021], which is primarily the use of VNC (like TightVNC) to allow remote access or SMB/Windows Admin Shares. Admin Shares are an easy way to share/access tools and malware. These are hidden from users and are only accessible to Administrators. Threat actors using Cobalt Strike almost always place it in an Admin share.
Exploitation of Remote Services [T1210] - mainly consists of abusing internal remote desktop (RDP) after initial access has been made. Internal RDP is the quickest method for a threat actor to move from host to host, especially if they already have domain administrator credentials.
Lateral Tool transfer [T1570] primarily correlates to the use of PSexec, which is a legitimate windows administrative tool. Threat actors leverage this tool to move laterally or to mass deploy malware across multiple machines.
Command and Control [TA0011]: Command and Control consists of techniques that adversaries may use to communicate with systems under their control within a victim network. Adversaries commonly attempt to mimic normal, expected traffic to avoid detection. There are many ways an adversary can establish command and control with various levels of stealth depending on the victim’s network structure and defenses
Remote Access Software [T1219]: Ransomware threat actors will use legitimate software to maintain an interactive session on victim systems. Common tools observed in Q3 were AnyDesk, TeamViewer, LogMeIn and TightVNC.
Ingress Tool Transfer [T1105]: When establishing command and control, actors will commonly install external tools onto the controlled endpoint in order to further proliferate their movement inside a network.
Credential Access [TA0006]: Credential Access techniques involve theft or malicious access and control of credentials like account names and passwords. Techniques used to get credentials include keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.
Brute Force [T1110]: Threat actors will run scripts or programs that attempt authentication access by trying millions of username and password combinations until one works. Brute forcing is primarily run against servers that have an open Remote Desktop (RDP) port (internal or external)
OS Credential Dumping [T1003]: OS credential dumping typically occurs after access has already been gained. The most popular tool used by threat actors, regardless of what group they may be associated with is Mimikatz, but there are several others that can accomplish the same goal of harvesting progressively more privileged account credentials. High impact attacks require threat actors to compromise senior level administrative credentials.
Execution [TA0002]: Execution techniques involve adversary-controlled code running on a local or remote system. Techniques that run malicious code are often paired with techniques from other tactics to achieve broader goals, like exploring a network for lateral movement or exfiltrating data. For example, an adversary might use a remote access tool to run a PowerShell script that does Remote System Discovery.
Command and Scripting Interpreter [T1059]: Scripting is mostly seen with the use of Cobalt Strike when executing a payload. Cobalt Strike is an incredibly common and powerful offensive security tool that is seen on 20-40% of ransomware attacks.
Common Industries impacted by Ransomware in Q3 2022
The increased prevalence of Hive ransomware in Q3 2022 accounted for the increase in attacks on health care organizations. Unlike some groups, Hive does not even attempt to steer clear of impacting health care facilities and displays a general ambivalence to the potential kinetic outcomes that their attacks may have on patient care. A notable subset of healthcare attacks were also attributed to BlackCat, Black Basta, and Vice Society - groups that, prior to Q3 2022, tended to avoid impacting enterprises in this sector. Their collective pivot towards this higher-profile sector could indicate more desperate economics of running a profitable ransomware brand, particularly as the average outcome of a ransom payment for victims continues to decline in quality and reliability.
Q3 2022 was marked by a sharp increase in suboptimal outcomes, including decryption flaws, permanent data loss and re-extortion events wherein companies who paid an agreed upon sum were re-extorted days or weeks later by the same adversary. Re-extortion has historically been a forecastable tactic, used principally by small game ransomware actors who can withhold keys from certain systems. The tactic is amateur to the point that most mid-big game hunting ransomware affiliates avoided ever using it out of fear it would damage their reputation. While most re-extortion demands are low Q3-2022 marked Coveware’s first quarter with multiple re-extortion demands in the millions committed by well-known big game actor groups.
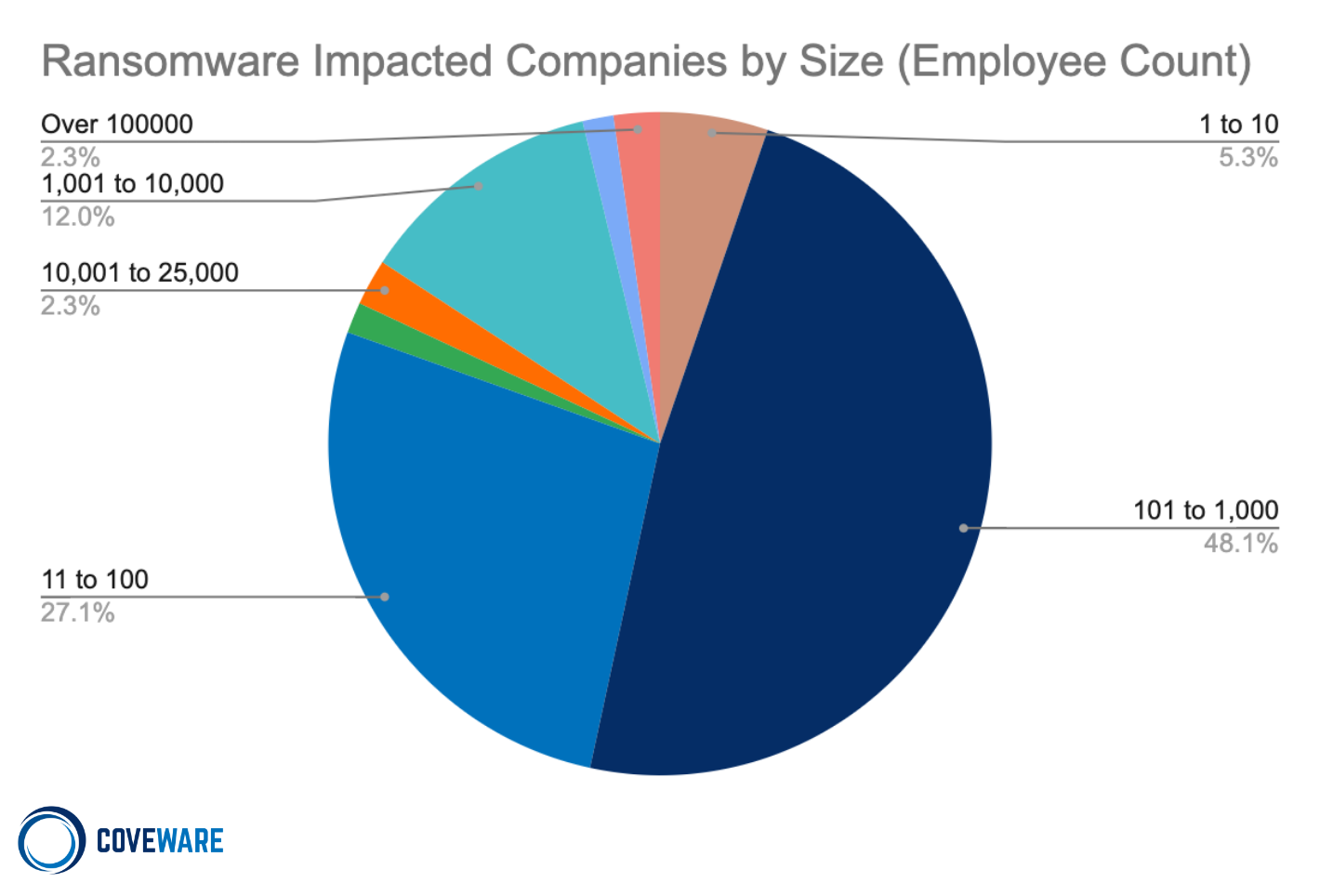
Average and Median Size of Companies Impacted by Ransomware in Q3 2022
Deeply impactful attacks remain a major risk for mid market and small organizations. Larger companies are still succumbing to extortion attacks, but the impact tends to be much more limited to just data exfiltration.
Ransomware is still a small business problem and disproportionately impacts smaller companies. The average days of downtime was ~25 days in Q3 of 2022, reflecting the amount of time an impacted company may experience some non-zero level of disruption from the attack.