Why Zero-Day Downstream Mass Data Extortion Campaigns are Losing Their Bite
Q4 of 2025 was marked by the latest large-scale data theft campaign by the CL0P ransomware gang, this time exploiting a zero-day vulnerability in Oracle E-Business Suite (EBS). The campaign came from a playbook CL0P pioneered nearly five years ago. The strategy involves: purchase a zero-day exploit of a widely used enterprise file transfer or data storage appliance, compromise as many instances as possible before detection, exfiltrate as much data as possible from as many downstream customers as possible, and finally monetize at scale the attack through extortion of each unique downstream party. This strategy does not involve the encryption of the target assets. Often the entire attack chain occurs outside of the victim’s network. This was the 5th campaign where CL0P followed this playbook, and the financial outcome for CL0P tells an interesting story about the current state of cyber extortion.
CL0P developed this playbook during the Accellion breach in Q1-2021. At the time, data exfiltration-only extortion was still a relatively novel tactic. Most cyber extortion attacks in 2020-2021 involved the encryption of critical systems as the primary driver of extortion pressure. Increasingly, actors during this period of time were combining encryption and data exfiltration extortion to compound the pressure on victims to pay. At this point in cyber extortion, data exfiltration was a very effective pressure tactic. Victims lacked confidence in their ability to assess what had been taken, regulators were still adapting to breach notification rules and enforcement, and many organizations viewed payment as a pragmatic way to make the problem “go away.”
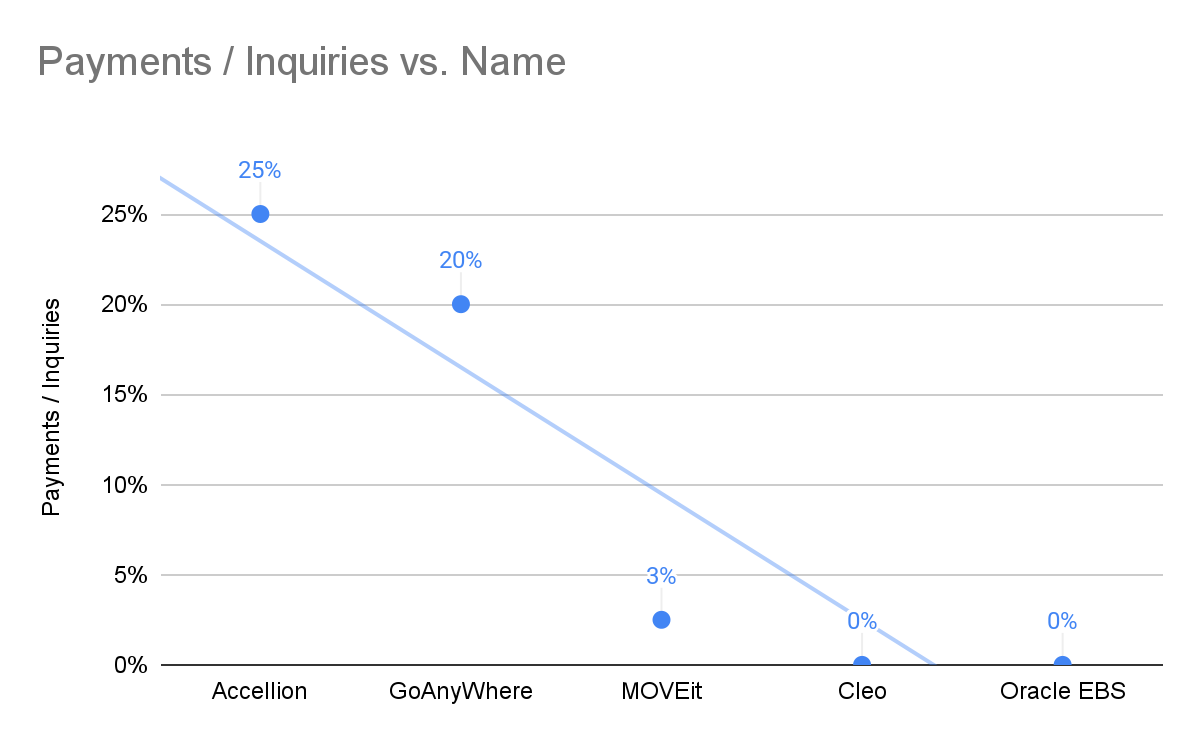
CL0P’s first campaign was likely very successful financially. It was reported that the exploit used traded for a few hundred thousand dollars. We estimate that the payment rate on the Accellion campaign was close to 25%. Given the volume of organizations impacted (100+), it is likely CL0P earned tens of millions of dollars from this single campaign. CL0P duplicated this success in March of 2023 by exploiting a vulnerability in GoAnywhere MFT. During that incident it is likely 100-150 organizations were impacted, and close to 20% of them ended up paying. A few months later, CL0P captivated the enterprise security media with yet another massive campaign. Between 2000-3000 organizations were impacted directly or indirectly by an extortion campaign that exploited a zero day in MOVEit managed file transfer software. Despite the daily headlines, few organizations ended up paying (we estimate ~2.5%). By 2024 though, when CL0P exploited a vulnerability in the Cleo Managed File Transfer product, organizations had matured. The propensity to pay a ransom under these circumstances had dropped. Despite several hundred downstream organizations being impacted, Coveware recorded no victims that opted to pay. With each iteration, the economics of downstream mass data theft weakened substantially.
Statistics are based solely on cases Coveware handled directly. Industry wide statistics and experiences may differ.
There is no single variable that explains why these campaigns are no longer bearing financial fruit for cyber criminals. During MOVEit, many victims were able to independently reconstruct what data had been accessed or exfiltrated, reducing their reliance on threat actors for visibility. In the Cleo campaign, the data itself turned out to be of relatively low sensitivity, limiting extortion leverage. But the Oracle EBS campaign in 2025 disrupted those assumptions.
In many ways, Oracle EBS represented a return to “ideal” extortion conditions from the attacker’s perspective. Victims generally lacked the forensic ability to reconstruct what had been stolen, and the data stored in these environments was often operationally and commercially sensitive. In 2021, those factors would have correlated strongly with high threat actor engagement and payment rates. Instead, the Oracle EBS campaign in 2025 generated one of the lowest levels of victim engagement and monetization observed across any prior CL0P incident.
Enterprises are getting educated on the pros and cons of paying a ransom to suppress the release of already breached data. The bullet points on the ‘pro’ side of the white board are getting increasingly scarce, while the cons side is getting crowded.
Over the past several years, organizations have matured significantly in their understanding of breach consequences. Paying for data suppression does not eliminate legal or regulatory notification obligations. It does not meaningfully reduce the likelihood of litigation. And experience has shown—repeatedly—that it does not prevent threat actors from retaining the data, selectively leaking it, or recycling it for future re-extortion months or even years later. The perceived certainty that once justified nuisance or opportunistic payments has been replaced by a clearer view of the long-term risk. Additionally, even engaging the threat actors in a dialog now carries substantial risk. The harassment tactics used by cyber criminals once they are engaged are getting increasingly bold, and kinetically dangerous to the organizations (such as SWATTING attacks against executives).
Other threat actors have attempted to replicate CL0P’s model with similarly disappointing financial results. The Snowflake-related breaches in 2024 and the CRM-focused attacks in 2025—largely attributed to Shiny Hunters—impacted organizations globally. Despite the scale and visibility of these incidents, extortion payments remained the exception rather than the rule. Most victims received cogent advice from skilled lawyers and incident responders, and opted not to even engage the threat actors. The ransom notes were tossed in the waste bin after a rational discussion in front of the white board.
As breach attorneys and defenders become more realistic about what can be achieved from an extortion payment—and organizations become more confident in managing breach fallout without negotiating—the economics of these data theft campaigns have eroded. Exploiting a single vendor flaw to reach hundreds of victims no longer guarantees hundreds of potential paydays. For enterprises, that realization may be one of the most meaningful defensive evolutions of the past five years.
Looking ahead: ransomware payment rates are at record lows and what worked during the double-extortion boom of the early 2020s no longer produces consistent or substantial profits for ransomware and extortion actors. We expect a pivot; threat actors may return to their data encryption roots, which has always been a more effective lever than data extortion at increasing the chance of payment. They may diversify how they use and monetize access to victim networks, beyond direct extortion. And we expect they will continue to downsize their respective operations to minimize overhead costs and risks.
Ransom Payment Amounts in Q4 2025
Average Ransom Payment
+57% from Q3 2025
Median Ransom Payment
+132% from Q3 2025
Trend Analysis:
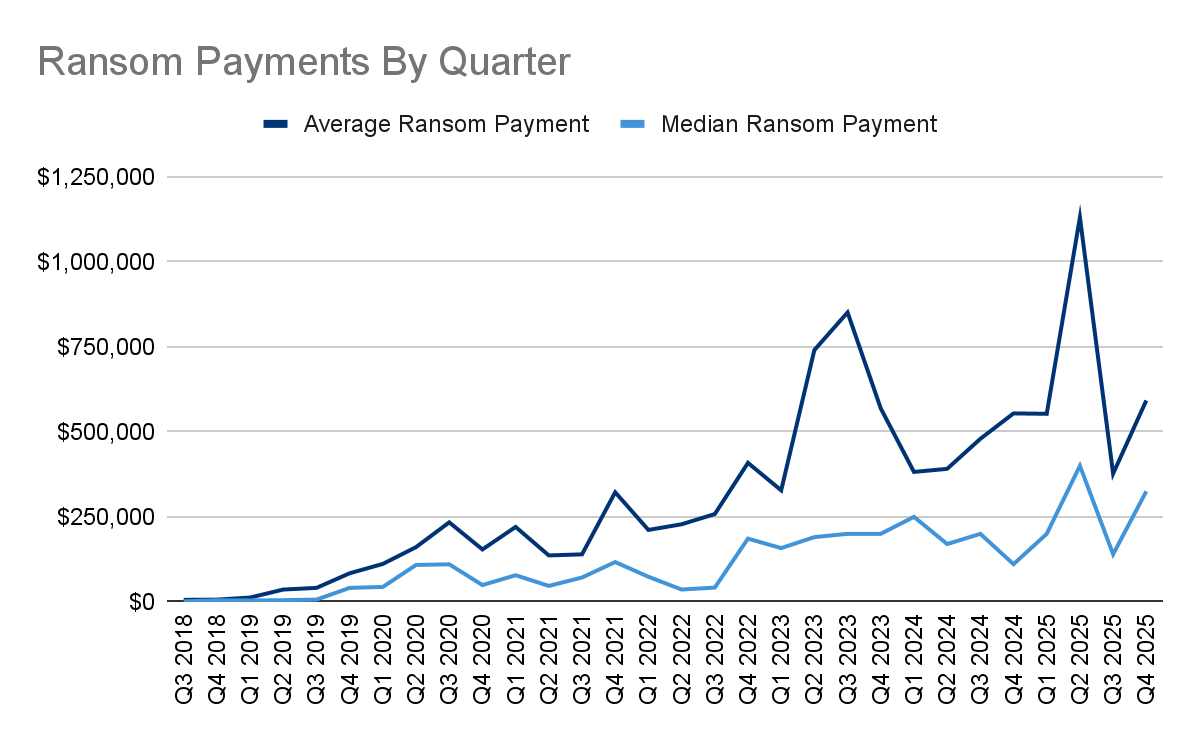
Average and Median Payments Diverge, Reinforcing Skewed Economics Q4 continues to show a pronounced gap between average ($591,988, +57% from Q3 2025) and median ransom payments ($325,000, +132% from Q3 2025). While median payments remain comparatively constrained, the average payment exhibits sharp volatility driven by a small number of outsized settlements. This reinforces that headline “average ransom” figures are increasingly influenced by edge cases rather than representative outcomes.
Large, Sporadic Payments Drive Spikes, Not Broad Willingness to Pay The pronounced spikes in average payment reflect isolated, high-impact incidents, typically tied to decryption-motivated settlements where business interruption could not be otherwise mitigated. These events are not indicative of a broad resurgence in willingness to pay, but rather the residual cost of severe operational disruption in a subset of cases.
Median Payments Remain Anchored to Mid-Market Reality Median ransom payments continue to track materially lower than averages, aligning with a victim mix dominated by small and mid-sized organizations. These organizations are more likely to pay when impacted, but are structurally limited in the amounts they can sustain, reinforcing a volume-driven extortion economy rather than a return to big-game hunting economics.
Data Theft Alone Rarely Drives Large Settlements Consistent with prior quarters, the chart supports the continued decline in high-value settlements driven purely by data exfiltration pressure. Payments remain primarily correlated with operational downtime and recovery constraints, not the perceived value of suppressing stolen data, an outcome increasingly understood by larger, more mature organizations.
Impact, Not Size, Remains the Primary Cost Driver Despite periodic spikes, the underlying trend remains intact: company size does not reliably predict ransom size. Instead, payment magnitude continues to correlate most strongly with incident impact, particularly the loss of critical systems, ineffective backups, and prolonged recovery timelines, further undermining the economic assumptions behind traditional big-game hunting strategies.
Payment Rates in Q4 2025
Trend Analysis:
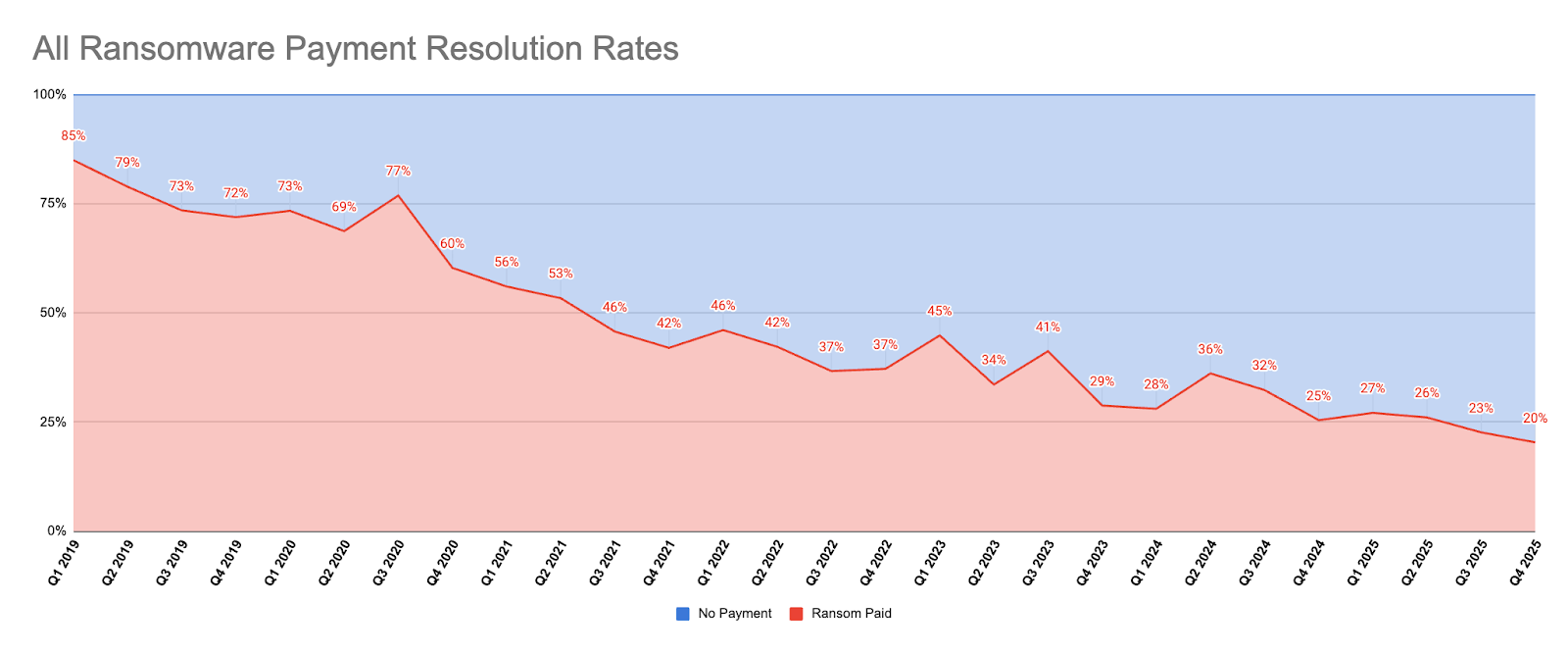
Ransom Payment Rates Continue to Set New Lows Ransom payment rates have continued their long-term decline, reaching approximately 20% in the most recent quarter, representing a new historical low and extending the multi-year downward trajectory observed since 2020.
Operational Resilience Is Reducing Reliance on Decryption Keys Organizations, across both enterprise and mid-market segments, are increasingly able to withstand encryption-driven disruption and restore operations without relying on a threat actor’s decryption key. This reflects tangible improvements in backup integrity, recovery planning, and incident response execution.
The “Plateau” is Downward Sloping Where payment rates previously oscillated in the 25–35% range, the most recent data indicates a clear break below that band. Rather than short-term volatility, the trend now suggests a structurally lower equilibrium for ransom payments across impact scenarios, including encryption and data exfiltration.
Starving the Extortion Economy Requires Collective Discipline Each avoided ransom payment removes oxygen from the cyber extortion ecosystem. The cumulative effect of improved prevention, reduced blast radius, and disciplined response decision-making continues to erode attacker economics, particularly for volume-driven RaaS operations.
Decline Reflects Maturity, Not Reduced Threat Activity This downward trend should not be misinterpreted as a reduction in attack frequency. Instead, it reflects improved organizational maturity: better preparation, stronger recovery options, and a growing recognition that ransom payment, particularly to suppress stolen data, offers diminishing utility.
Sustained Pressure Is Essential to Long-Term Impact Contracting the cyber extortion economy requires continued pressure from defenders, insurers, advisors, regulators, and law enforcement. While zero may remain an asymptote rather than an immediate destination, the trajectory demonstrates that coordinated effort can materially weaken attacker incentives over time.
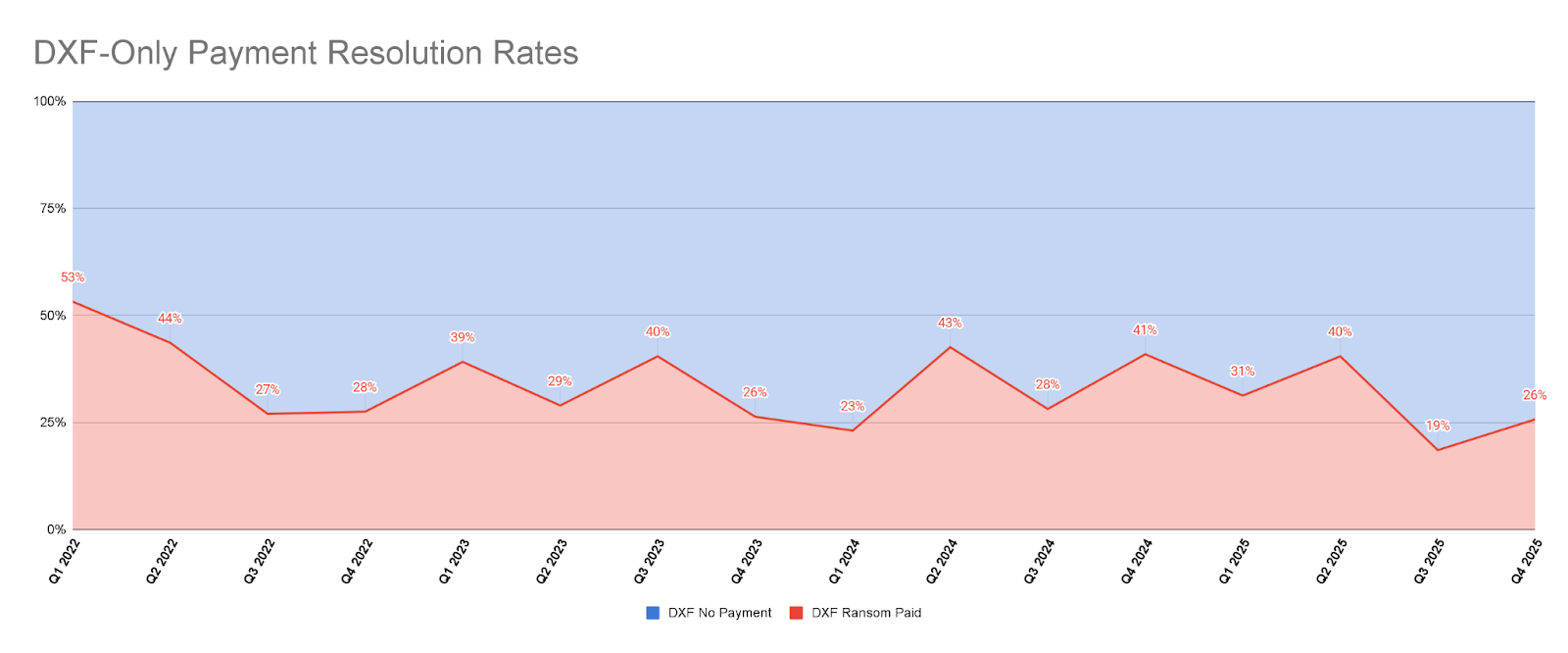
Data Exfiltration-Only Payments Remain Structurally Low Despite Short-Term Volatility While DXF-only payment rates show quarter-to-quarter fluctuation, the most recent data point sits at approximately 25%, remaining well below historical norms and reinforcing that data-theft-only extortion continues to convert poorly for threat actors.
Non-Payment Is Now the Default Starting Position The sustained suppression of DXF-only payment rates reflects a meaningful shift in incident response posture. Enterprises increasingly begin data-exfiltration incidents from a default assumption of non-payment, rather than treating payment as a primary mitigation lever.
Growing Consensus That Paying Does Not Reduce Risk Experience and investigation continue to validate that ransom payment offers little to no durable benefit in DXF-only cases:
Stolen data is frequently retained, resold, or re-leveraged, regardless of payment
Commitments to suppress or delete data are routinely unverifiable
Payment does not reliably prevent future targeting or secondary extortion
Re-Extortion and Data Recycling Undermine Cyber Criminal Trust Economics As the pool of high-value, solvent victims contracts, threat actors increasingly revisit known victims or resell stolen data to third parties. This erodes the already fragile trust model underpinning DXF-only extortion and further weakens payment as a rational control.
Threat Actor Pressure Is Economic, Not Reputational DXF-only campaigns persist not because they are highly successful, but because they are cheap to execute and scalable. Lower operational costs allow actors to tolerate poor conversion rates while applying broad pressure across many victims.
Strategic Implication for Defenders The data reinforces a critical principle: DXF-only extortion is best managed as a legal, regulatory, and communications challenge, not a negotiation problem. Investments in breach response planning, privacy counsel readiness, and stakeholder communications continue to deliver higher return than ransom payment.
Most Common Ransom Variants in Q4 2025
| Rank | Ransomware Type | Market Share % | Change in Ranking from Q3 2025 |
|---|---|---|---|
| 1 | Akira | 14% | - |
| 2 | Qilin | 13% | - |
| 3 | Lone Wolf | 12% | - |
| 4 | Cl0P | 7% | New in Top Variants |
| 5 | Silent Ransom | 6% | New in Top Variants |
| 6 | Shiny Hunters | 4% | -2 |
Market Share of the Ransomware attacks
Consistent with our discussion of why zero-day downstream campaigns are losing their efficacy, it is interesting to note that the top two variants in Q4 (who have held that spot for several quarters now) both employ encryption as the primary impact driver. Both exfiltrate data as well, but encryption is the primary source of leverage. Slots 3-6 on the market share board are data exfiltration only actors. As data exfiltration only attacks yield less and less financial success, we expect Akira, Qilin and other actors that rely on encryption to be relatively more successful vs. data exfiltration only groups.
Most Common Initial Attack Vectors in Q4 2025
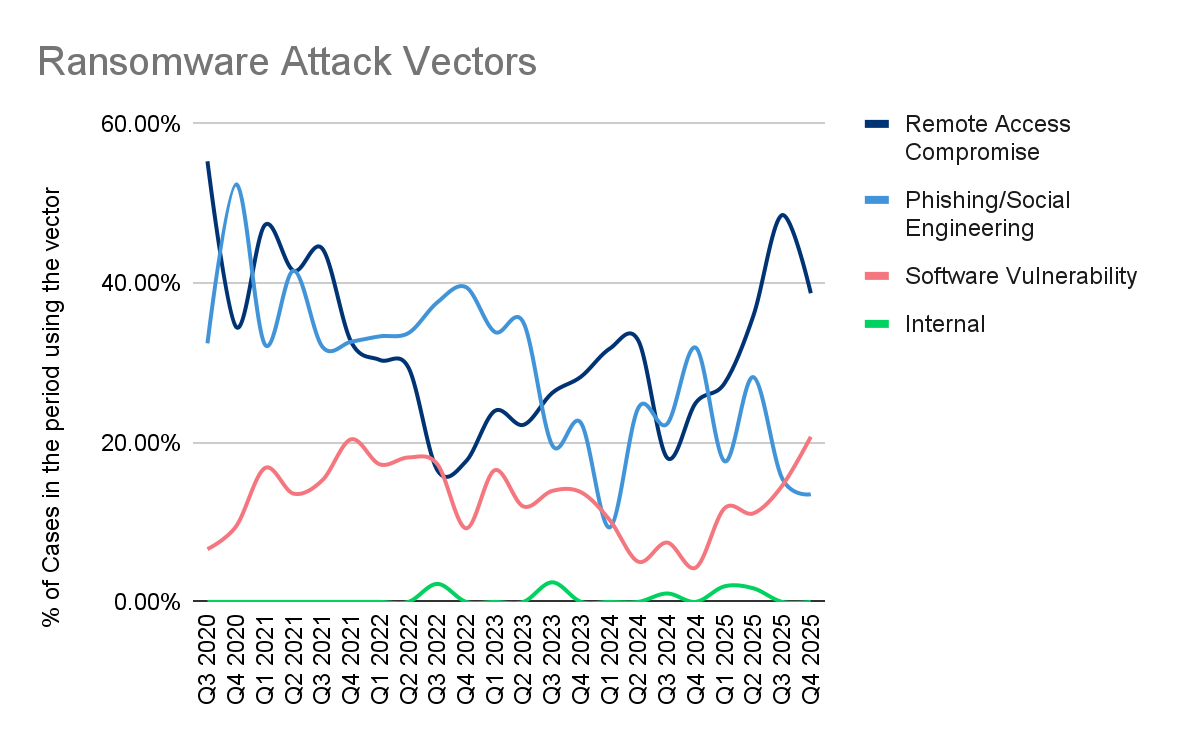
Remote access compromise remained the dominant initial access vector in Q4 2025, reaffirming that attackers overwhelmingly favor identity-backed footholds over malware-driven entry. What “remote access” represents has fundamentally changed: beyond VPNs and RDP, it now encompasses SaaS administrative access, OAuth tokens, API integrations, and delegated trust relationships. Attackers are not breaking controls so much as operating within them: logging in, being provisioned, or inheriting access through workflows designed for legitimate use. Most compromises succeeded not because systems were unpatched, but because configuration debt persisted: stale credentials, legacy local accounts after migrations, and insufficient visibility into cloud identity and token usage.
Phishing and social engineering appeared to decline in Q4, but this reflects absorption into remote access outcomes rather than reduced attacker reliance on human trust. Social engineering has become the enabling mechanism for durable access, convincing help desks to issue credentials, obtaining OAuth consent, or legitimizing attacker activity inside SaaS platforms. As a result, campaigns increasingly register as remote access compromise instead of phishing, despite people remaining the critical control failure. Q4 activity continued to demonstrate how impersonation, vishing, SEO poisoning, and abuse of trusted vendors or integrations allow attackers to establish long-lived, platform-native access with minimal technical indicators prior to data theft.
Software vulnerability exploitation continued its slow but consistent rise in Q4, remaining less frequent than credential-based access but disproportionately impactful when successful. While Cl0p’s zero-day campaigns contributed to the rise, most exploitation activity was opportunistic, capitalizing on delayed patching, incomplete migrations, exposed management interfaces, and residual credentials. Even fully patched environments were compromised when legacy access paths remained open. Once exploited, these footholds often led quickly to data exfiltration or lightweight ransomware deployment, reinforcing that exploitation today is less about persistence and more about speed to impact.
Q4 2025 reinforces that identity is the primary intrusion surface, not endpoints or malware, and that social engineering, SaaS access, and remote footholds are now inseparable elements of the same access problem. The majority of successful breaches still stem from failures in process, trust, and access hygiene rather than missing tools or signatures. Defense strategies that prioritize identity controls, access governance, and visibility across both infrastructure and SaaS, alongside patching, are better aligned with how attackers actually gain and retain access today.
Most Common Tactics, Techniques and Procedures Threat Actors used in Q4 2025
Lateral Movement [TA0008]
Lateral movement remained one of the most consistently observed tactics in Q4 2025, appearing in 65% of cases and continuing to serve as the operational backbone of modern intrusions. The decline from Q3 does not signal reduced adversary reliance, but more likely reflects faster containment and improved visibility earlier in the attack lifecycle. Threat actors continue to abuse legitimate administrative protocols and tooling (e.g., RDP, SSH, PSExec, and native management utilities) to expand access, escalate privileges, and position themselves for data theft and encryption.
Exfiltration [TA0010]
Exfiltration remained a defining feature of extortion operations in Q4, observed directly in 61% of cases, despite a notable decline from prior quarters. This apparent reduction masks the underlying reality: confirmed data exfiltration occurred in 94% of incidents overall, and in 62% of cases where encryption was present. The statistical drop reflects quieter, faster exfiltration methods, increased cloud- and SaaS-based intrusions, and a continued shift toward extortion-only pressure models rather than reduced attacker interest in data theft.
Defense Evasion [TA0005]
Defense evasion re-entered the Top 5 in Q4, observed in 43% of cases, reflecting attacker prioritization of remaining undetected long enough to complete staging and exfiltration. Techniques increasingly targeted endpoint controls, identity telemetry, and logging gaps, allowing adversaries to suppress early warning signals while operating within legitimate tooling and workflows. The resurgence of defense evasion aligns directly with the high rate of confirmed exfiltration in Q4, underscoring that successful extortion now depends as much on minimizing detection as it does on gaining access or deploying payloads.
Impact [TA0040]
Impact tactics declined again in Q4, appearing in 41% of observed cases, but this remains a visibility artifact rather than a reduction in attacker intent. Encryption was still confirmed in the majority of incidents, with 68% of cases involving encryption. As in prior quarters, forensic evidence of impact is frequently lost in virtualized and cloud-heavy environments where administrative lockouts, rapid rebuilds, and system reinstalls erase telemetry. The data reflects a growing gap between observed impact and real-world disruption, not diminished operational damage, as attackers continue to manipulate or destroy backups to amplify pressure during negotiations.
Credential Access [TA0006]
Credential access appeared in 39% of Q4 cases and remains a consistent enabler tightly coupled with lateral movement, defense evasion, and exfiltration. Credentials are often reused, replayed, inherited, or obtained through trust relationships rather than freshly harvested, blurring traditional kill-chain sequencing. This identity-centric access model supports the high rate of confirmed exfiltration by allowing attackers to move and operate without triggering conventional alarms. Credential abuse in Q4 reinforces that identity protection is a control-plane problem rooted in access governance, lifecycle management, and visibility, not merely an authentication challenge.
Most Common Industries Impacted by Ransomware in Q4 2025
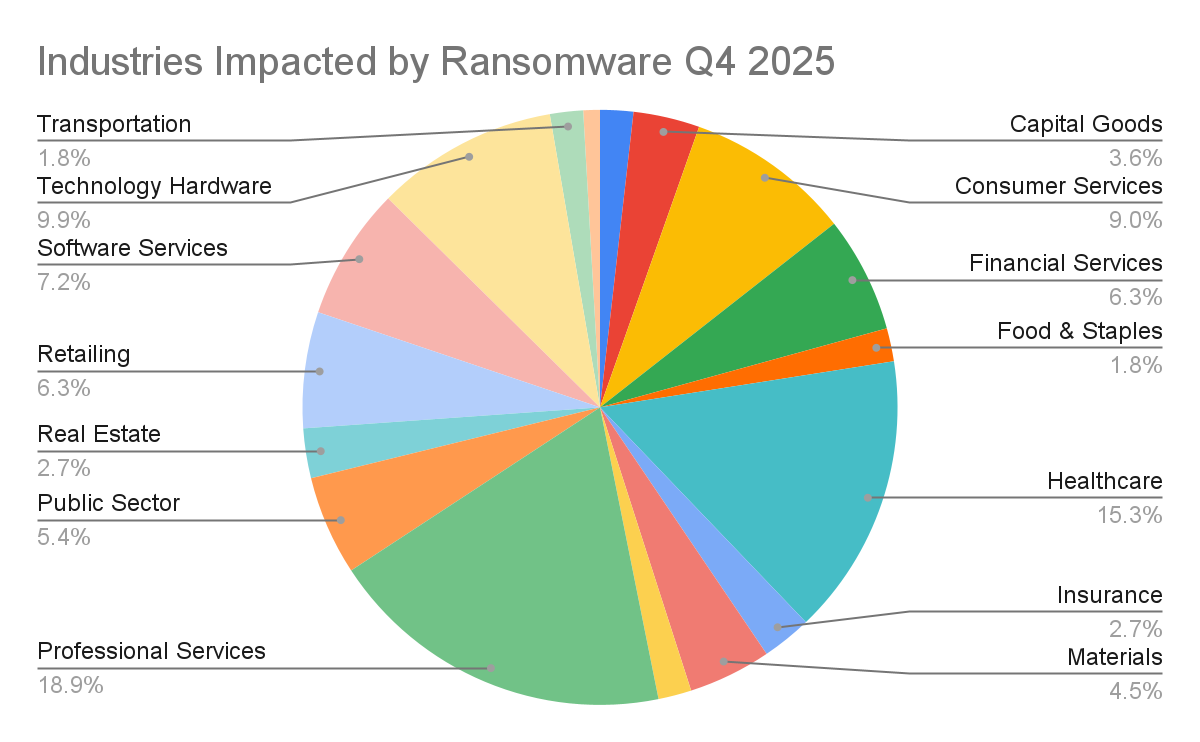
In Q4 2025, ransomware activity was unevenly distributed across industries, with a clear concentration in service-oriented and operationally critical sectors. Professional Services experienced the highest share of attacks at 18.92%, followed by Healthcare at 15.32%, reflecting attackers’ preference for targets with high downtime sensitivity and pressure to restore operations quickly. Technology-related sectors also featured prominently, including Technology Hardware & Equipment (9.91%) and Software Services (7.21%), alongside Consumer Services (9.01%). Financial Services and Retailing each accounted for 6.31% of observed attacks, while the Public Sector represented 5.41%. In contrast, asset-heavy or more regulated industries such as Utilities (0.90%), Automotive (1.80%), Transportation (1.80%), and Media (1.80%) saw comparatively lower levels of activity, underscoring a continued attacker focus on sectors where disruption translates most directly into leverage.
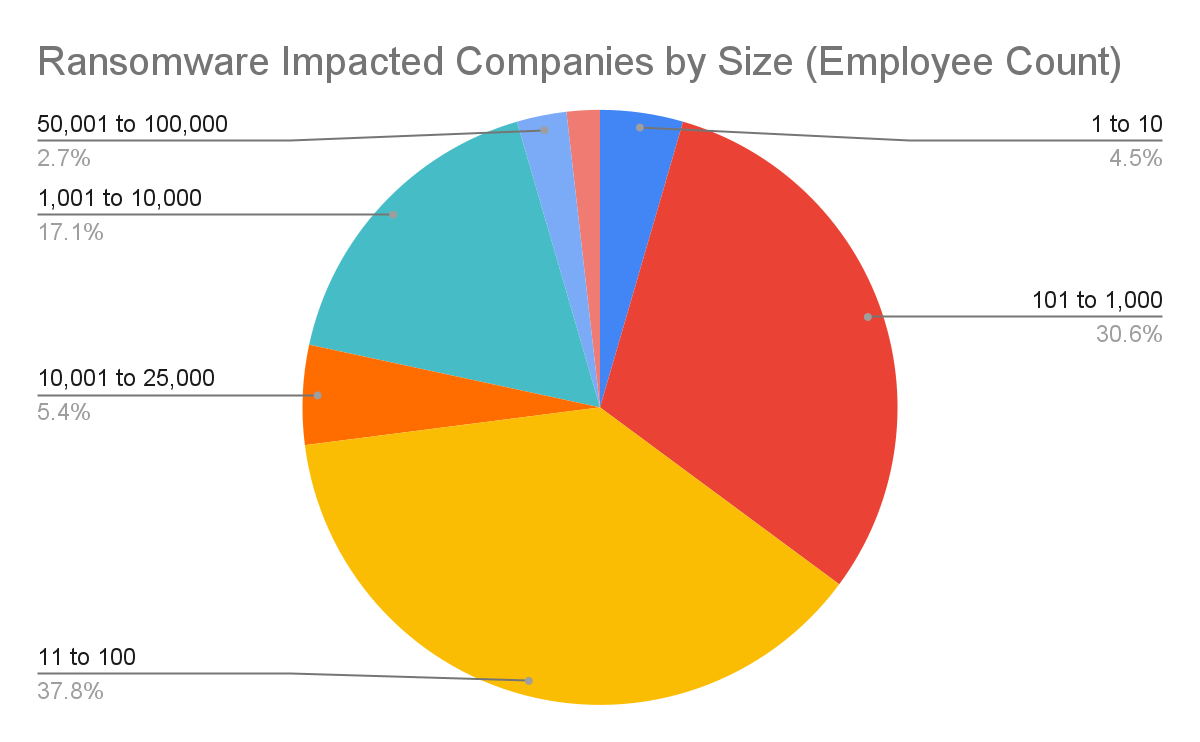
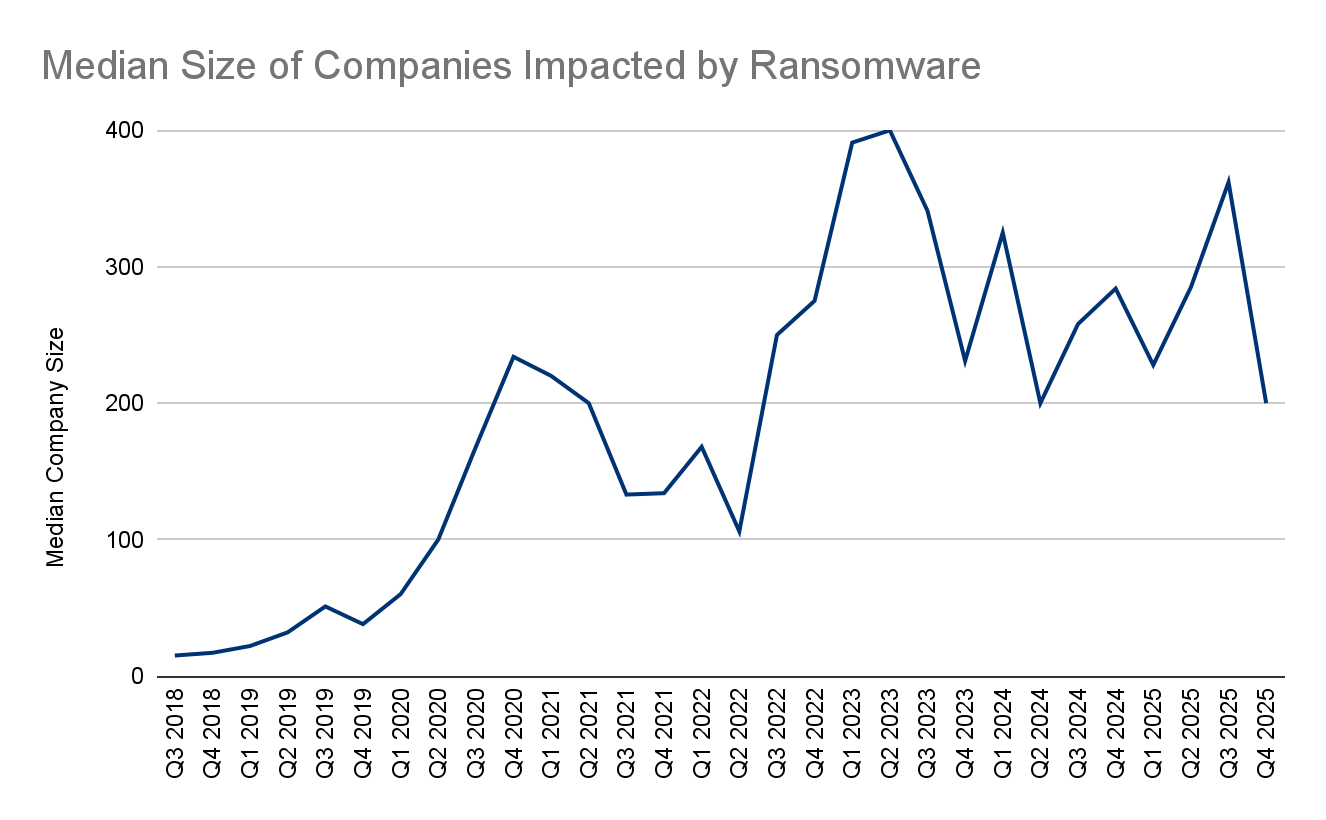
The Median company size impacted by a ransomware attack in Q4 2025 was 200 employees (-45% from Q3 2025). Ransomware incidents in Q4 2025 were most heavily concentrated among small and mid-sized organizations, highlighting attackers’ continued preference for targets with limited security resources and high operational exposure. Companies with 11 to 100 employees accounted for the largest share of attacks at 38%, followed closely by organizations with 101 to 1,000 employees at 31%. Mid-market firms with 1,001 to 10,000 employees represented another 17%, reinforcing that the bulk of ransomware activity sits well below the enterprise tier. By contrast, very large organizations were attacked far less frequently, with companies over 100,000 employees accounting for just 2% of cases and those with 50,001 to 100,000 employees at 3%. Notably, organizations in the 25,001 to 50,000 employee range saw no observed incidents, underscoring how ransomware campaigns continue to skew toward smaller, more numerous, and operationally constrained targets rather than the largest global enterprises.