Decrypt Ryuk Ransomware. How to Recover Ryuk Encrypted Files
Ryuk Ransomware has exploded in prevalence in 2019, and is now the most common type of ransomware to impact medium- to large-sized businesses. Ryuk is a type of Hermes Ransomware, and was previously associated with the Lazarus group, an attribution that has since been all but discredited. Given its prevalence, it’s important to understand how a Ryuk ransomware attack occurs, and the steps that must be followed if a victim needs to pay the ransom and run the decryption tool.
How Do Ryuk Attacks Happen?
The majority of Ryuk Ransomware attacks can be traced back to either Remote Desktop Protocol access or email phishing as the attack vector. This is due to the prevalence of poorly secured RDP ports and the ease with which ransomware distributors are able to gain access, either by brute force or by purchasing credentials on dark market sites. Companies that allow employees or contractors to access their networks through remote access without taking the proper protections are at a grave risk of being attacked by Ryuk Ransomware. Email phishing is also increasingly prevalent in Ryuk attacks. Exploit kits such as Trickbot and Emotet are increasingly used by attackers to procure elevated credentials which allow them to encrypt the entire network of a targeted organization. A typical attack follows the pattern below:
Example of the Ryuk Executable along with PsExec and Batch file
Subordinated user access is gained via brute forced RDP or Phishing an employee
Elevated credentials are harvested using Trickbot, Mimikatze or other software. This allows the Ryuk attackers to move laterally in order to surveil the network and map machines, domain controllers and general topography.
Domain controllers are used to store a copy of PsExec, an instance of the Ryuk executable, and a batch script to the domain controllers and other valuable components of a victims network.
Using PsExec the attacker copies a batch script to a folder on all accessible machines across the victim’s environment. The attacker then uses PsExec to copy the Ryuk binary to the Root directories of these machines. A new service is created to launch the Ryuk binary and started.
The Ryuk executable begins encrypting files on impacted systems resulting in all affected machines becoming encrypted and leaving the readme.txt files and corresponding ransom notes.
How Does Ryuk Encrypt Files?
Ryuk uses a three-tier trust encryption model. The first tier / foundation is the global RSA key pair held by the attackers. The private key from this key pair is not available to the victim until the ransom is paid decryptor is purchased. The second tier is a RSA key unique to the victim. Most types of ransomware generate this key during the encryption process, and encrypt the resulting private key using the global key. With Ryuk, the ransomware arrives with the key pre-installed and the private key pre-encrypted. The third tier is a standard AES symmetric encryption key generated for each victim file using the Win32API function CryptGenKey. This key is then exported using CryptExportKey. It is encrypted using the second-tier key, and the encrypted result is appended to the encrypted file.
How Do You Identify If Ryuk Has Encrypted Your Files?
Ryuk Ransomware typically appends a standard ‘.ryk’ to encrypted files. There is known to be one variant which does not append any special extension to the files, but it uses the same encryption method as the standard Ryuk that does append ‘.ryk’ to the files.
An encrypted file would follow the below pattern (example of a word document):
Filename.doc.ryk
Ryuk Ransomware typically leaves behind an elongated ransom note that explains what has happened and identifies itself at the end of the note.
Components of a Ryuk Ransom Note
Example of a Ryuk Ransom Note
Ryuk Message to the IT Team
At the top of the ransom note, the attackers are specifically calling out the IT team in an effort to intimidate them. They warn that there is no method of decryption (this is true at the time of writing this), and not to try any of the standard ways to recover the data.
Free Proof of Ryuk Decryption
In the next section, the note calls out the ease of decryption should the victim opt to pay. The time frame given is not exactly accurate given how difficult the Ryuk decryptor is to operate, and the length of time Ryuk cases typically take to recover. The attackers offer a proof of decryption for a small file, which is pretty much standard.
How to Obtain Bitcoins to Pay a Ryuk Ransom
Ryuk ransomware notes do not provide guidance on how to obtain Bitcoin, unlike other types of ransomware. The attacker’s first response to a victim over email typically has more information on how to obtain Bitcoins.
Contacting the Ryuk Attacker
At the conclusion of the note, contact information for the attacker is provided. Most of the time there are two email addresses given. The majority of Ryuk distributors change their email addresses for every attack, so there is rarely a repeat.
There is currently no free decryption tool for Ryuk ransomware and no commercial software capable of decrypting the files. Be leery of any company that claims to be able to decrypt Ryuk using proprietary methods. When a victim of Ryuk pays the ransom, the attackers typically provide a link to a file sharing site and some written instructions. The attacker’s instructions are usually an oversimplified 4-step process like below. In reality, the process is much more complicated.
Example Ryuk Decryption Instructions
1. Disable antivirus, firewalls, stop the mysql server services (in case the databases were encrypted), etc.
2. Connect all shared folders that were encrypted.
3. Execute decryption software with administrator privileges.
4. Click "2", then press Enter and wait, decryption will be performed in automatic mode.
In step #1, the attacker is instructing the victim to disable anti-virus software and firewalls on the machine that is downloading or running the decryption tool. This is unnerving, but accurate as the decryptor executable will be quickly flagged or blocked by any form of endpoint protection that is active on the affected machine. The instructions also tell the victim to pause SQL DB activity. It is very common for SQL databases to become corrupted during the initial encryption process. Unfortunately, it is very hard to determine if this corruption has actually occurred until after the SQL DB files are decrypted.
In step #2, the attacker is instructing the victim to reconnect any mapped or mounted drives to the machine that has encrypted the files. It is very common for ransomware victims to disconnect machines in the hope of preventing the executable file from hitting other machines on the network. For the purposes of running the decryption tool, it is okay to reconnect mapped or mounted drives as long as those drives are not connected to any clean machines or environments. Because the Ryuk encryption malware is likely still active on your machines, great care must be taken at this step.
In step #3, the attacker is instructing the user to ensure they run the decryptor as administrator. Permission and read/write access is necessary for the decryptor to properly decrypt files, so running as administrator is required.
In step #4, the attacker is giving generalized advice on how to run the decryptor across all detected machines and drives. In practice, it does not work nearly that seamlessly. Please, see our more detailed write up below on how to run and point the decryptor.
How to Use The Ryuk Decryptor Tool
(Please note that the below is just an example and not a guide or guarantee that should be relied on in any way. Ransomware variants and their decryptors evolve weekly and this example may be obsolete or conflict with instructions a hacker provides. Please, see our Terms of Service for further disclaimer).
The Ryuk decryptor is unreliable and riddled with errors that reside within the code. These issues make the victims’ user experience running decryption very challenging and time consuming. Some of the most prominent issues are:
Windows file path spaces: If there is a space in the Windows file path, the decryptor will fail the decryption process.
Quotation “ marks in file path: If there is a quotation mark (“) in the file path the decryptor will report an error that it cannot find the specific file.
Windows Version function: The decryptor uses the “GetVersionExW” function to determine the Windows version, for Windows 8.1. The value returned by this API has changed and the decryptor isn’t designed to handle this value.
.Ryk extension removal: The decryptor doesn’t remove the .ryk extension and replace it with the original extension. Since there is no way to determine the original file type based just on the file name, it can be extremely labor intensive for enterprise victims to fully rename and restore their files.
Infinite loop in manual mode: When choosing the manual option in the decryptor, the user has to supply a path of the specific file or choose “0” to finish. However, choosing a “0” will put the decryptor into an infinite loop.
Running the Ryuk Decryptor
Step 1) Enter password. After launching as admin the decryptor will prompt for a password. Enter the password provided:
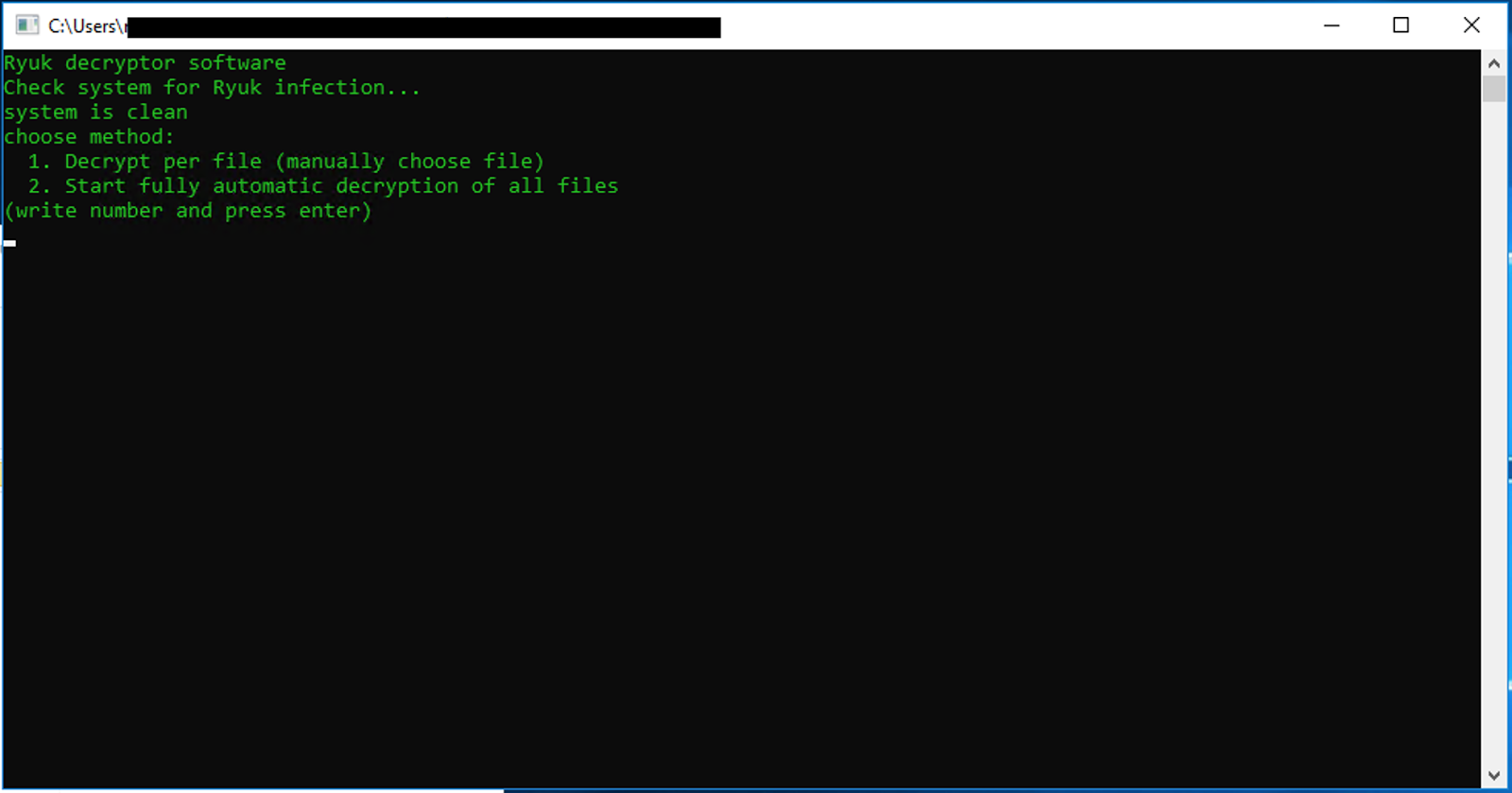
Step 2) Once launched the first thing the decryptor does is to search the HKEY_CURRENT_USER Hive for a value pair named “svchos” in the path “SOFTWARE\Microsoft\Windows\CurrentVersion\Run” and delete the specific entry. This removes the Ryuk executable. Afterwards it will reboot the system and remove any remaining Ryuk malware still on the system. Once rebooted the user needs to run the tool again and the decryptor will provide two options to decrypt.:
Decryption per file
Automatic decryption
Step 3) When selecting the first option, the decryptor can be pointed at a specific file or folder. Once you specify the file the decryptor will locate and decrypt the file, notifying you when it is done by asking for the next file.
Step 4) The second option will attempt to run the decryptor across all connected drives and shares. However, it is not uncommon that the process will fail and need to be restarted or repointed.
Step 5) Once complete the decryptor will notify you and force you to exit the executable.
Step 6) Check and repeat. After exiting, it is up to the technician to review which files were properly decrypted and which were not. Files that failed will need to be replaced from the backup (remember to make another copy). Large files may need to be pointed to directly, using method number one in the decryptor.
If you are experiencing a ransomware incident involving Ryuk or any other variant, please don’t hesitate to reach out for help.