Sodinokibi Ransomware Poised to Impact Larger Enterprises
In late April, a new variant of ransomware, Sodinokibi, was observed exploiting CVE 2019-2725, a deserialization vulnerability in Oracle WebLogic Server. The vulnerability allows remote code execution without authentication. Vulnerabilities of this sort are particularly dangerous, as they enable remote code execution without the need for a username and password. Oracle issued a patch outside of their normal patch cycle given its severity. It is uncommon for ransomware designed for financial crime to utilize a zero-day exploit. This is mainly due to the cost of purchasing the exploit before it is released, or the sophistication needed to scale attacks relative to other, softer vulnerabilities, such as insecure RDP configurations, or email phishing campaigns; both of which are relatively inexpensive. Cisco’s reporting on Sodinokibi’s use of a zero-day highlighted an anomaly in the typical distribution pattern of financially motivated ransomware. Given the sophisticated attack vector and the investment the developers of Sodinokibi have made to their payment TOR site, this variant seems to be poised to become a popular choice among ransomware distributors.
Sodinokibi Distribution Tactics Poised to Evolve into Mainstream Ransomware Channels?
The primary attack vectors for ransomware have remained relatively stable over the past two quarters. The predominant vectors for small businesses continue to be brute forced RDP sessions, while upmarket email phishing experienced a resurgence in Q1. The combined use of email phishing and exploit kits such as Trickbot, Emotet, or credential stealers like Vidar have commoditized breached network access for ransomware distributors. We previously noted that the inclusion of GandCrab into some of these multifaceted exploit kits, and a corresponding increase in the number of unique GandCrab IDs per attack. For example, in the ConnectWise / Kasaya attacks the number of unique IDs in a single network skyrocketed and caused major issues for victim and GandCrab operators alike. Sodinokibi appears to have addressed these ‘scaling issues’. The encryption process does create multiple IDs, with multiple encrypted file extensions and corresponding TOR pages, BUT a single decryptor can be issued to decrypt the entire network of extensions, regardless of the number of IDs. This overcomes a major shortcoming of the GandCrab payload, and we would not be surprised if GandCrab affiliates rotate to Sodinokibi as a result. It also appears that initial Sodinokibi victims are larger enterprises than the typical GandCrab victim. The ransom amounts have been larger than GandCrab, more akin to the big game hunting M.O. of Ryuk ransomware.
Sodinokibi Ransom Notes and Encrypted File Extensions
After Sodinokibi completes the encryption process, a ransom note similar to the one below is posted to affected machines.
GandCrab appends a random string of letters to encrypted files - each combination corresponding to a ransom note with the same extension. Sodinokibi is similar. Encrypted file names will include a 5-9 character alpha-numeric extension, corresponding to a ransom note with the same extension name.
Each ransom note lists two websites, one hosted on TOR and one not. The note directs the victim to visit the TOR site. The non-TOR site has the domain http[:] //decryptor[.]top/ and is hosted by Reg.Ru, a leading Russian domain registrar and hosting service.
Sodinokibi Ransomware TOR Site Features
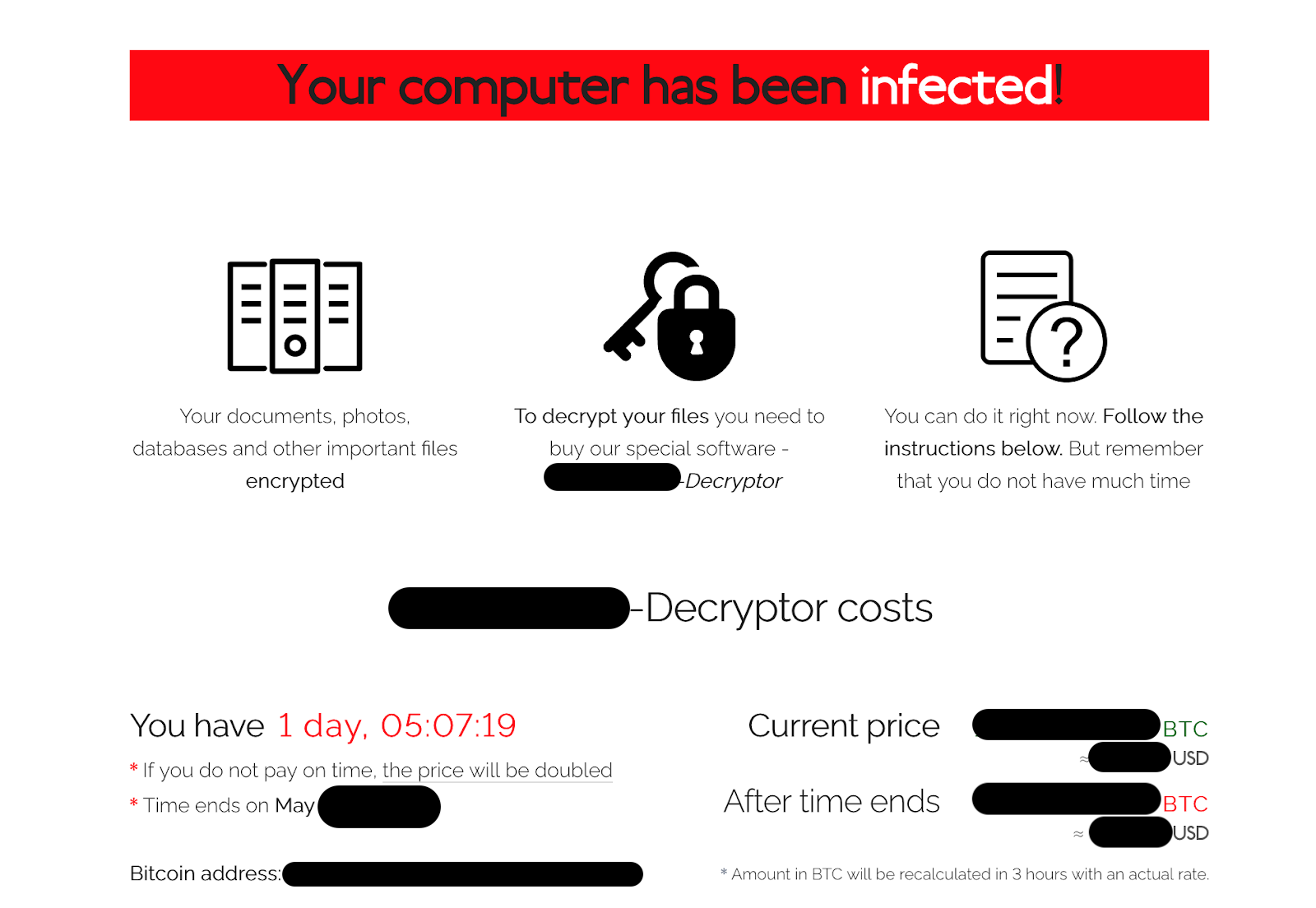
The features of the Sodinokibi TOR site appears simpler than GandCrab. Below is a screenshot of the landing page:
The page includes the current ransom amount in Bitcoin and in USD. Similar to GandCrab, the USD amount is pegged and the corresponding BTC amount is refreshed every couple of hours. There is a fixed period of time until the amount doubles. It is not immediately apparent if the Sodinokibi TOR site has features that enable dishonest data recovery companies to skim from their victims, but we would not be surprised if they surface.
When a Sodinokibi infection leaves behind multiple IDs, each ID will have a corresponding TOR site. However, unlike GandCrab, the price on all of the Sodinokibi TOR sites is the price for all of the victim’s IDs. GandCrab enables payment for a single ID (so one segment of a network can be decrypted as a standalone), this does not appear to be the case with Sodinokibi. Its all or nothing.
Another key difference between Sodinokibi and GandCrab is the utility of the decryptor. A single Sodinokibi decryptor has the private key of the victim and decrypts all of the victim’s IDs. GandCrab requires a unique decryptor for each ID. As previously mentioned, this was a particularly cumbersome limitation during the the ConnectWise / Kasaya attacks as hundreds of unique decryption tools would often have to be run on large networks.
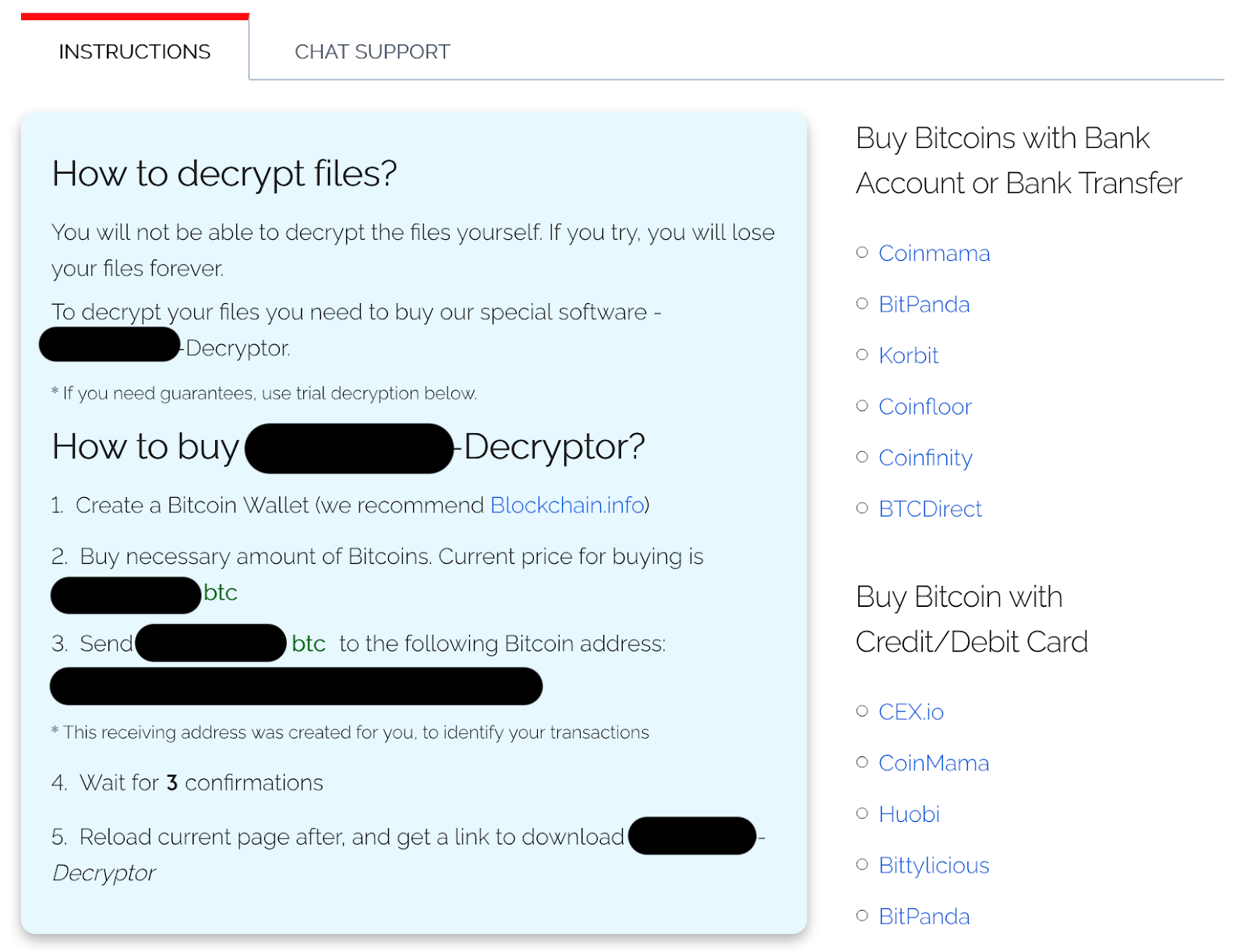
Sodinokibi Ransomware TOR Site Instructions
Below the fold, the Sodinokibi provides more formal instructions on the extortion and recovery process. The instructions describe how to purchase the decryptor, how to decrypt sample files and list venues to purchase cryptocurrency.
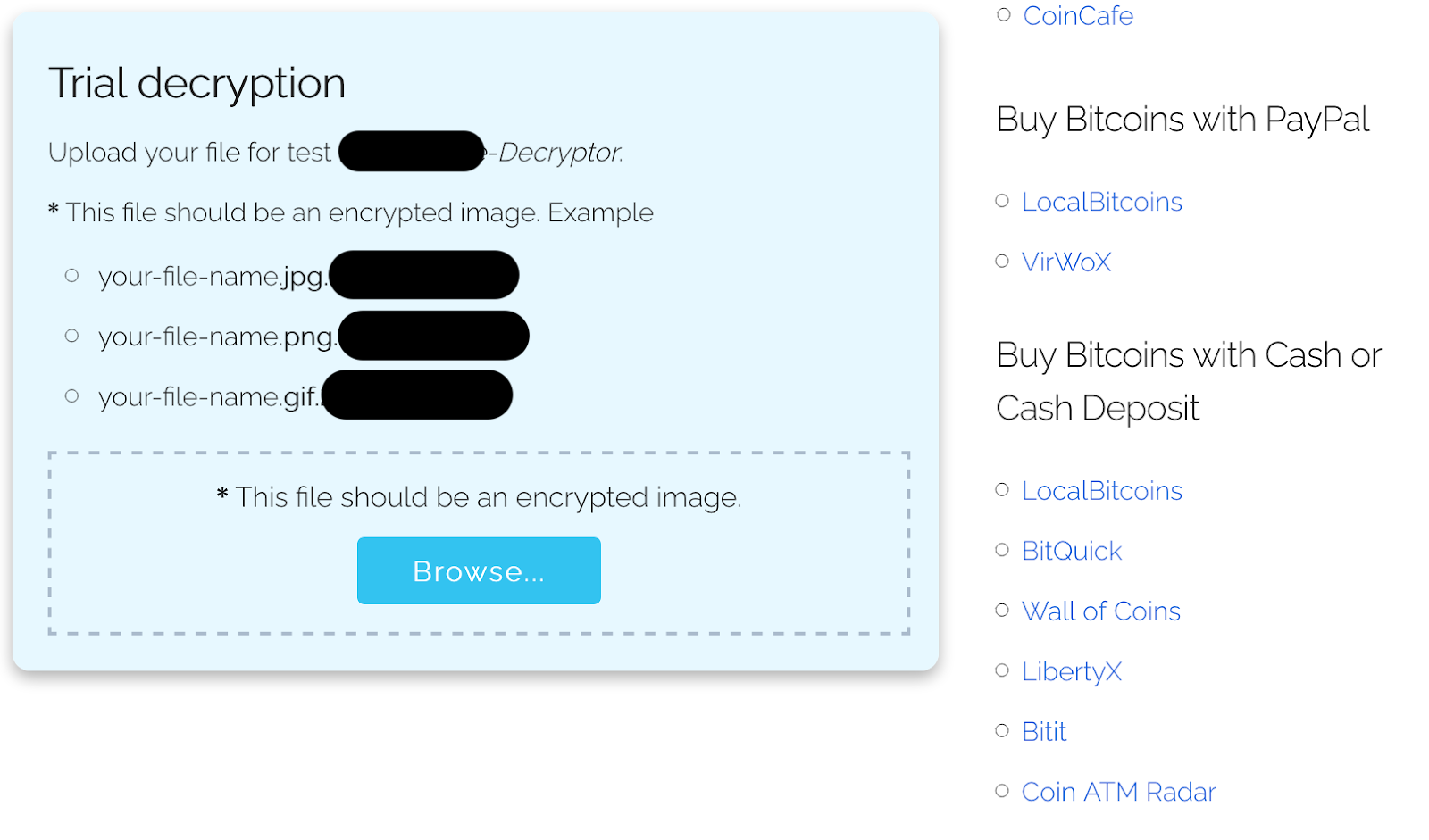
Sodinokibi File Decryption Test
Similar to GandCrab, the Sodinokibi TOR offers proof of file decryption. The victim may upload a small image file and the site will return it decrypted. An image of this feature is below:
Sodinokibi Ransom Payment
The Sodinokibi page is rigged to trigger an updated screen once the BTC transaction to the listed wallet is confirmed. While awaiting payment confirmation the screen will appear similar to the image below:
Similar to GandCrab, the page releases the decryption tool after 3 blockchain confirmations. Unlike GandCrab, the page displays the number of confirms, so it simple to know when to refresh the page and download the decryptor.
Sodinokibi Decryptor Release With Private Keys
After three blockchain confirmations, the page can be refreshed and decryptor download instructions are provided. The page appears as below:
Prior to downloading, the all encrypted file extensions on the victim’s network can be pasted into the dialogue box. This adds final instructions to the tool and helps ensure it identifies all extensions.
Running the Sodinokibi Decryption Tool
Despite the enhancements to the TOR site, the Sodinokibi decryption tool is just as painfully slow as GandCrab’s. Among ransomware decryption tools, the two are the slowest. Large drives often take several days to decrypt. The decryption instructions provided were updated to describe how to decrypt specific drives.
When the decryptor is opened the initial state is as below.
The command line will list the encrypted file extensions provided before download. However, in our tests, we observed the tool decrypted extensions that were NOT populated in the dialogue box as well. While the decryptor runs the file count will increment.
Similar to GandCrab, the ‘create backup’ checkbox denotes that a copy of the encrypted file is made before decryption begins. This can be a helpful feature if certain files are prone to decryption failure, but bear in mind it will require 2x the amount of space as each file will exist twice. When the decryptor completes, the user gets a successful pop-up.
As always, paying a ransom should be the absolute last resort. Victims are encouraged to explore every plausible recovery method before paying a ransom. Carefully archiving a full copy of the encrypted data is recommended as a first step. Please review our ransomware response guide, or contact us if you are in need of immediate assistance.