Q4 2020 Doxxing Victim Trends: Industrial Sector Emerges as Primary Ransom “Non-Payor”
The analysis that follows is based on an examination of ransomware doxxing victims whose identities were published between September and December of 2020. The data for this blog post was collected from 100% public sources. Unlike the majority of research on cyber extortion trends, which is based on information collected from self-identified victims of ransomware, these data points are collected from the threat actor’s own public ledgers of victims and are not subject to the same limitations of self-reporting. At this time one year ago, only two or three ransomware gangs had developed the practice of naming-and-shaming victims who failed to pay the ransom.
Now, nearly two dozen ransomware families host dedicated data leak websites, where the names and files of their allegedly non-paying victims are published in perpetuity. In this report, we examine key victimology attributes, including geography, sector, employee count and reported revenue, and if and how these trends have shifted in the last six months.
Doxxing Data Geography
Companies based in the United States remained the most represented in the doxxing data by a significant margin. After the US, victims from the UK, Canada, France and Germany were the next most represented; this is true for the most recent dataset, as well as for victims who were published in Q2/Q3 of 2020.
| Rank | Country | Market Share of Doxxed Victims | Change in Rank Since Q2/Q3 |
|---|---|---|---|
| 1 | USA | 55.8% | - |
| 2 | Canada | 7.4% | +1 |
| 3 | France | 6.9% | +1 |
| 4 | UK | 5.2% | -2 |
| 5 | Germany | 4.8% | - |
| 6 | Italy | 3.7% | +2 |
| 7 | Australia | 1.7% | -1 |
| 8 | Brazil | 1.4% | -1 |
| 9 | India | 1.2% | New in Top 10 |
| 10 | Mexico | 1.2% | New in Top 10 |
Top 10: Market Share Doxxed Victims
While the majority of ransomware groups mirrored the aggregate trends of victim geography, CL0P remained a consistent outlier, with 43% of their victims coming from Germany and only 28.6% coming from the US. This distinct distribution has remained stable for CL0P over time. This fact aligns with intelligence that CL0P is the ransomware weapon of choice for certain advanced persistent threat (APT) groups who are more likely to target victims in advance based on perceived value, industry and location. The way these victims are selected is decidedly different from traditional ransomware “targets” who are more often compromised indiscriminately and en masse by commodity malware campaigns, and later sold or shared with ransomware partners for potential extortion.
Figure 1. CL0P Victims by Region in Q4
At the beginning of 2020, Nephilim stood out alongside CL0P as an outlier whose victims predominantly came from non-US regions such as Brazil (21.4%). In Q4, their focus fell much more in line with the status quo – 55.6% of the victims are coming from the US. Nephilim ransomware still showed a propensity for heavier victim targeting in other areas (revenue, company size), but from a regional standpoint, they seem to have shifted their sights to US victims, like many of their counterparts.
Figure 2. Nephilim Victims by Region in Q2/Q3
Figure 3. Nephilim Victims by Region in Q4
Doxxing and Industry Distribution
For as long as we have been studying ransomware victims, the largest industry cohort represented has been companies in the non-essential goods and services sector, particularly those in the professional services industry. However, in Q4, we observed a slight but statistically significant pivot in these trends in which the professional services industry dropped into second place. In its stead, the industrial services industry became the most prominent cohort displayed on the public leak sites. Of the subset of industrial victims, those in engineering and construction were the most commonly victimized (32.5%), followed by machinery (16%) and transportation and logistics (15%).
Doxxing Victims by Sector, Q4 2020
Doxxing Victims within Industrial Sector, Q4 2020
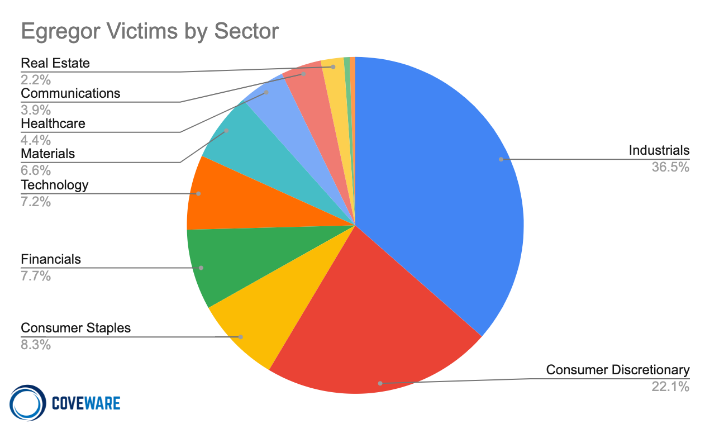
Of note, companies in the industrial sector became the top doxxing targets for DoppelPaymer, Netwalker, and Sodinokibi who had previously favored companies in non-essential goods and services. Additional contributors to this market shift included the Maze group, which increased their margin of industrial victims from 28.3% in Q2/Q3 to 40% in Q4, and newcomer Egregor, whose first quarter in operation yielded 36.5% industrial sector victims and only 22% in consumer discretionary.
We note that this discovery diverges from the findings outlined in our Q4 report, which showed that professional services remained the most victimized sector, albeit at a slightly reduced rate compared to Q3.
One likely factor for this discrepancy is that the doxxing data we examined is primarily limited to ransomware victims who refused to pay, whereas Coveware’s Q4 report encompasses victims who experienced a ransomware event, regardless of whether it resulted in a ransom payment. Since the doxxing data is comprised mainly of non-payors, perhaps this finding is less an indicator of who is being targeted and more an indicator of who is refusing to pay.
Companies in the industrial sector tend to maintain less sensitive data pertaining to their customer base and as a result, are less motivated to pay for data suppression. In contrast, companies in professional services, leisure services and retail are more apt to store sensitive financial data and potentially damaging customer information, which in turn makes them more likely to consider paying a ransom if it will reduce the odds of an embarrassing or damaging public data leak.
DoppelPaymer Victims by Sector, Q4 2020
Netwalker Victims by Sector, Q4 2020
Sodinokibi Doxxing Victims by Sector, Q4 2020
Egregor Victims by Sector, Q4 2020
Ransomware groups that demonstrated a more distinctive industry makeup of victims included CL0P, Mespinoza (PYSA) and Mount Locker.
CL0P
CL0p’s industry spread was the most unique. The energy and technology sectors made up only 2% and 6% of all Q4 victims, respectively, and yet CL0p’s victim pool was dominated by both. As discussed, researchers have identified that CL0P ransomware is weaponized by APT groups who are more prone to select victims based on their characteristics and marketplace position rather than on which company has the weakest point of ingress.
CL0P Doxxing Victims by Sector, Q4 2020
Mespinoza (PYSA)
Mespinoza stood out not for their most favored industry target (37.5% consumer discretionary), but for their disproportionate focus on public sector entities. Despite lopsided media attention that is paid to public sector attacks, they only comprised 5% of all doxxing victims in Q4. However, 19% of Mespinoza’s victims came from this sector, which is up from 12% of Mespinoza victims in Q2/Q3. Interestingly, as the margin of public sector victims increased, Mespinoza’s focus on healthcare victims dropped from 19.4% to 6.3% in the same time frame.
Mespinoza (PYSA) Doxxing Victims by Sector, Q4 2020
Mount Locker
Mount Locker made the “outlier” list due to one third (33.3%) of their posted victims coming from the healthcare industry, whereas healthcare victims only made up 6.3% of Q4 victims in aggregate. We note that all conclusions drawn about Mount Locker’s victimology should be tempered with skepticism, as they are one of the few groups that consistently posts the identities of victims submitted to them by other ransomware gangs. In other words, a company appearing on the Mount Locker site may not have been attacked by Mount Locker themselves. Usually, Mount Locker will tag the leak with a “Partner” footnote, to indicate a partner of theirs claims credit for the attack, but not always.
Mount Locker Doxxing Victims by Sector, Q4 2020
Doxxing by Revenue
Although there are several notable shifts within the revenue trends of specific groups, the aggregate numbers relating to revenue remained stable. The most represented cohort of victims were those reporting under $50 million in annual revenue, with non-revenue generating entities comprising the least represented category of victims. The ‘big fish’ billion dollar corporations made up only 8.5% of all targets, which is slightly lower than the 12% share they held in Q2/Q3.
Doxxing Victims by Reported Revenue, Q4 2020
Two thirds of the ransomware variants examined favored victims in the under-$50 million range above all others. Below are the ones who did not.
CL0P
Over 50% of CL0P’s victim pool reported earnings in excess of one billion dollars, which is more than triple the representation of the same cohort in CL0P’s Q2/Q3 victims. Once again, this comes as no surprise given their evident focus on their victims’ regional and occupational characteristics.
CL0P Doxxing Victims by Revenue, Q4 2020
Nephilim
Like CL0P, Nephilim demonstrated a heavy focus on lucrative enterprises with 44.4% of their targets coming from the $1 billion-and-above bracket. In further alignment with CL0P, you will not find any non-profits, public sector or other non-revenue-generating entities on their leak site.
Nephilim Doxxing Victims by Revenue, Q4 2020
While we expected to see this exaggerated focus on billion dollar companies from CL0P and Nephilim, we were surprised to see several more groups pivot their efforts in a similar direction. Defray777, a newcomer to the data leak scene, had 42.9% of their published victims in the billion dollar club and Sodinokibi, a veteran data leak group, nearly doubled their margin of billionaire victims from 11% in Q2/Q3 to 21.2% in Q4.
Defray777 Doxxing Victims by Revenue, Q4 2020
Sodinokibi Doxxing Victims by Revenue, Q4 2020
If we invert the lens and examine the market share across the highest revenue-generating victims, we find that Egregor comes in with the largest share (29.1%) with Sodinokibi following in second at 20%. It is significant that Egregor not only claims the most high-roller victims, but also has one of the shortest marketplace lifespans having only been in operation since September. The frequency with which they post new victims, and their excessive ownership of the wealthiest targets suggests they are deliberately seeking to extort victims of a certain financial capacity.
Market Share of Victims with Revenue over $1 billion, Q4 2020
Doxxing by Company Size
Unlike overall revenue trends which remained largely stable, there was a slight increase in the predominant company size of doxxing victims. 38.5% of victims fell within the 101-1000 employee bracket. In the preceding two quarters, companies with 100 or fewer employees were the most represented.
Doxxing Victims by Employee Count, Q4 2020
These metrics corroborate Coveware’s Q4 analysis of self-reported ransomware victims, which showed a 39% increase in the median company size since Q3. Ultimately, however, the data suggests that companies with 500 employees or less are still the most at-risk population for cyber extortion. The reasons for this remain consistent: limited resources allocated to cybersecurity and the misguided belief that because of their size and comparatively low profile market presence, they will not be targeted for ransomware attacks. Although the largest companies are the least represented (1.1%), it is worth examining the distribution of these victims by variant. The market share of companies with more than 50,000 employees is dominated by Egregor and Nephilim, followed by smaller ownership stakes held by Conti, Netwalker and Mount Locker. Given Nephilim’s laser focus on high-profile, high revenue-generating entities, their position here is somewhat expected. Egregor’s equal ownership, however, is more noteworthy.
Egregor has a diverse geographical and industry-based spread of victims, and yet also the highest market share of billion dollar corporations and companies with 50,000+ employees. They’ve been in operation for less than six months, and yet they also boast the highest volume of doxxed victims overall, even compared to ransomware groups that have been publishing victims for over a year. This suggests Egregor’s selection of targets is curated both with quantity and quality in mind, whereas most ransomware groups focus on one or the other.
Market Share of Victims with over 50,000 employees; Egregor, Nephilim, Conti, MountLocker, Netwalker.
Market Share of Doxxed Victims, Q4 2020
The final observation of note pertains to Sodinokibi. The company size makeup of Sodinokibi’s victims drastically shifted from Q2-Q3 (52% of victims having over 100 employees) to Q4 (69% of victims having over 100 employees). At first, we considered that the same spread of companies was being targeted and just the larger ones were refusing to pay and by extension, showing up more frequently in the doxxing data. Upon examining Coveware’s empirical data on both payors and non-payors of Sodinokibi ransoms, we discovered the average company size was effectively identical in both categories. This suggests that Sodinokibi is victimizing larger companies overall, and also aligns with the previously mentioned increase in Sodinokibi’s focus on billion dollar corporations in Q4.
Sodinokibi Doxxing Victims by Company Size, Q4 2020
Conclusion
The emergence of the industrial sector as the most represented doxxing victim sector in Q4 was a significant departure from years of empirical data that have shown non-essential goods and services companies as the most victimized by ransomware. Since the companies listed on these name-and-shame sites are predominantly composed of victims who did not pay the ransom, and because Coveware’s proprietary datasets of payors and non-payors show professional services to still be the dominant sector, we concluded this data point is likely the result of the industrial sector refusing to pay ransoms at a higher rate than their counterparts in discretionary retail and professional services. Companies specializing in construction, engineering, transportation and logistics are less likely to store highly sensitive or damaging employee and customer information and as a result, tend to be less intimidated by threats to release data publicly. At the variant level, Sodinokibi and Egregor stood out for their disproportionate focus on large and high revenue-generating targets while otherwise maintaining a diverse victim pool in terms of industry and geography.